This project provides a method of automating the AWS-Nuke tool into multiple accounts.
First and Final Warning: This is a dangerous and very destructive tool and should not be deployed without fully understanding the impact it will have on the accounts you allow it to interface with.
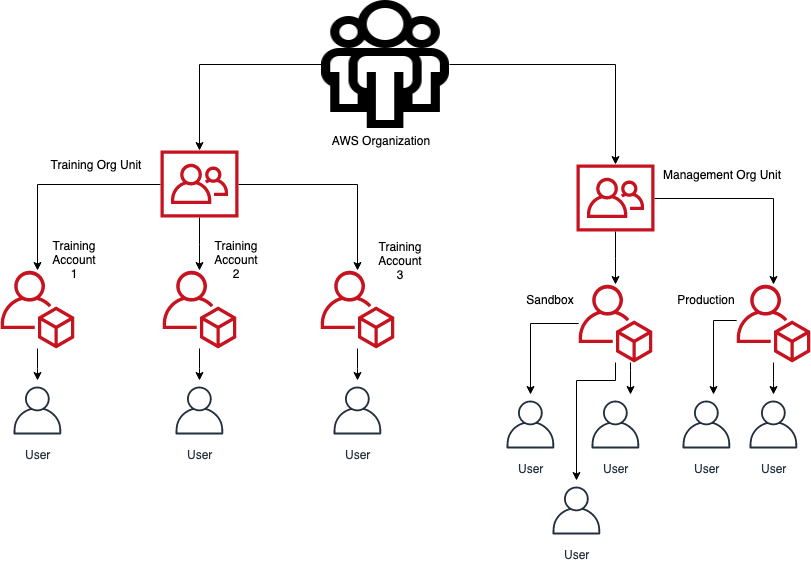
This tool was built with a specific organizational architecture in mind. See below for a visual overview. Specifically, take note that all training accounts are located withing a parent organziational unit, isolated from any other accounts in the organization.
By default this tool is configured to NOT be destructive, which follows a similar pattern to the AWS-Nuke tool's default behaviors. When deploying to Production, you need to modify the deployment code to allow AWS-Nuke to destroy resources on your behalf. See below for how and what to modify for Production:
### NukeStack.yaml (DEFAULT) ###
### Approx Line: 147/148 ###
# TODO: Add --no-dry-run flag for Production
aws-nuke -c $line.yaml --force --access-key-id $ACCESS_KEY_ID --secret-access-key $SECRET_ACCESS_KEY --session-token $SESSION_TOKEN |tee -a aws-nuke.log;Below is the Production code which needs to be in place for actually destroying resources in accounts:
### NukeStack.yaml (PRODUCTION) ###
### Approx Line: 147/148 ###
# TODO: Add --no-dry-run flag for Production
aws-nuke -c $line.yaml --force --no-dry-run --access-key-id $ACCESS_KEY_ID --secret-access-key $SECRET_ACCESS_KEY --session-token $SESSION_TOKEN |tee -a aws-nuke.log;- AWS CLI
- A firm understanding of AWS, and access to your organization's accounts
- A Role in each account to be cleaned that allows this CodeBuild Project to Assume permissions within the account. This Role needs to be consistently named across all affected accounts, as it's a parameter necessary for the CloudFormation template to run properly.
- Clone the repo
git clone https://github.com/1Strategy/automated-aws-multi-account-cleanup.git cd automated-aws-multi-account-cleanup - Determine the ID of the Organizational Unit that owns the grouping of accounts that you would like to cleanse with AWS-Nuke.
- Log into your AWS Account, and access the Organizations console to access the information regarding your organizational account structure.
- Note: You will need permissions to view this information
- Update your config file with specific filters for your accounts
- Note: It will be helpful to run aws-nuke locally a single account to ensure you have a firm grasp on resources that you would like to retain, such as roles for Administrator role assumption, as well as resources which will be destroyed.
- Run AWS-Nuke against one of your accounts with your updated config file to test the output.
- Note: By default, this is non-destructive.
# Example aws-nuke command (you will need to modify the config file, line 29, with an account number to run against) and subsequent output aws-nuke -c ./aws-nuke-config --profile sandbox Assume Role MFA token code: 000000 aws-nuke version v2.9.0 - Wed Mar 27 15:19:23 UTC 2019 - 0df913de92ab8f81646f06bfd0eadba0f42d722c Do you really want to nuke the account with the ID 000000000000 and the alias 'my-account-alias'? Do you want to continue? Enter account alias to continue. > my-account-alias global - IAMRole - AWSCloudFormationStackSetExecutionRole - filtered by config global - IAMRole - AWSServiceRoleForOrganizations - cannot delete service roles global - IAMRole - AWSServiceRoleForRDS - cannot delete service roles global - IAMRole - AWSServiceRoleForSupport - cannot delete service roles global - IAMRole - AWSServiceRoleForTrustedAdvisor - cannot delete service roles ... ... ... Scan complete: 104 total, 4 nukeable, 100 filtered. The above resources would be deleted with the supplied configuration. Provide --no-dry-run to actually destroy resources.
- The tool is currently configured to run at 12:00a PST Mon-Fri. It can be easily configured with a
rate()orcron()expression by editing the NukeStack.yaml file in theCloudWatchNukeScriptSchedule:Properties:ScheduleExpression:section. - Create an S3 Bucket and upload your
aws-nuke-config.yamlfileaws s3 mb s3://some-new-unique-bucket aws s3 cp ./aws-nuke-config.yaml s3://some-new-unique-bucket
- Deploy to production via aws cloudformation cli
aws cloudformation deploy \ --profile production \ --stack-name AccountNukeStack \ --template-file NukeStack.yaml \ --parameter-overrides \ ParentOuId=0-abcd1234 \ BucketName=some-new-unique-bucket \ AssumeRoleName=NukeRole - Retrieve the status of your stack
- Check the status of your build once:
aws cloudformation describe-stacks \ --profile production \ --stack-name AccountNukeStack \ --query "Stacks[*].StackStatus"- Or watch the status of your build over 5sec intervals:
watch -n 5 -d 'aws cloudformation describe-stacks --profile production --stack-name AccountNukeStack --query "Stacks[*].StackStatus"'
- Use aws cloudformation cli to remove the stack and all associated resources
aws cloudformation delete-stack --stack-name AccountNukeStack
Licensed under the Apache License, Version 2.0.