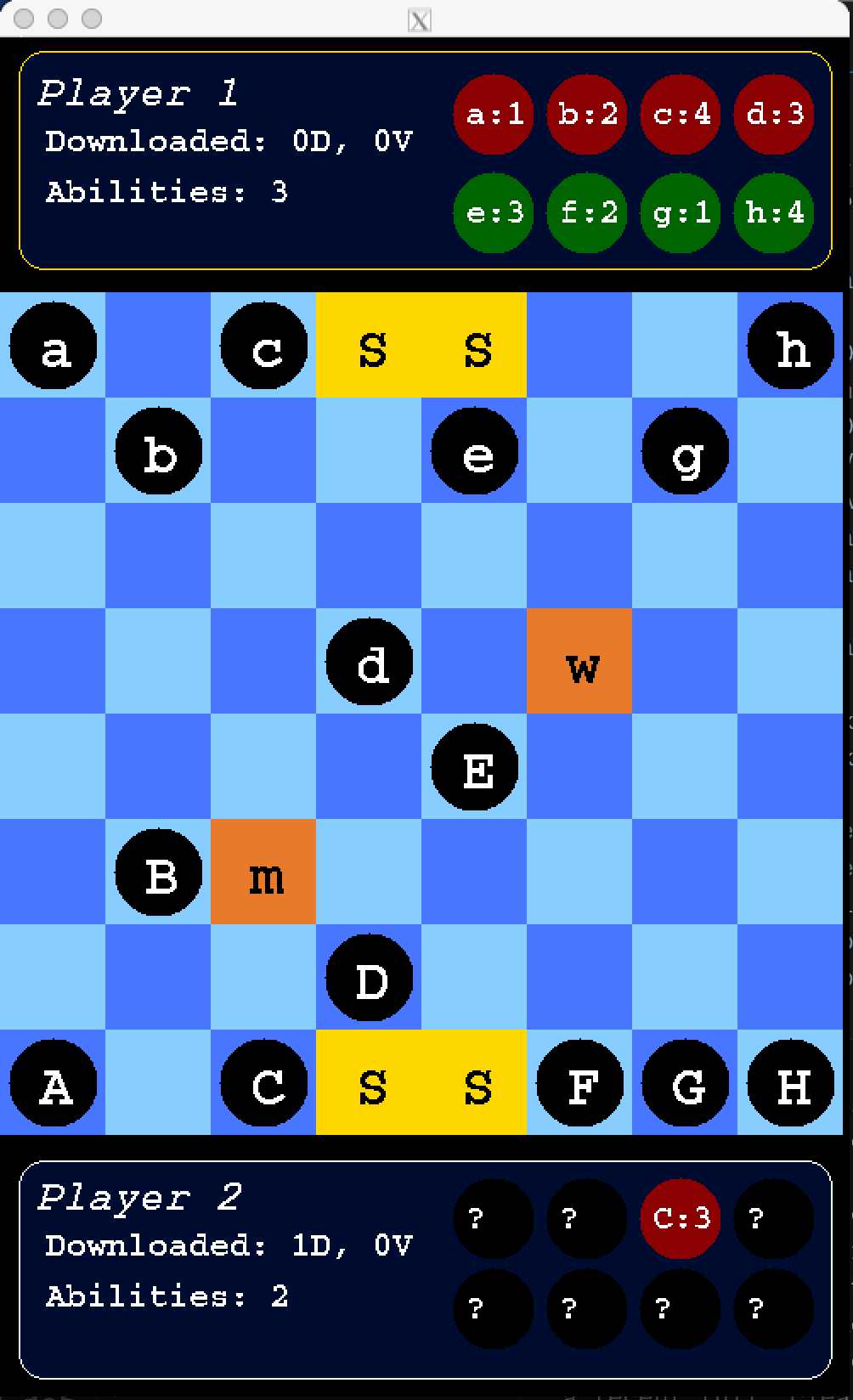
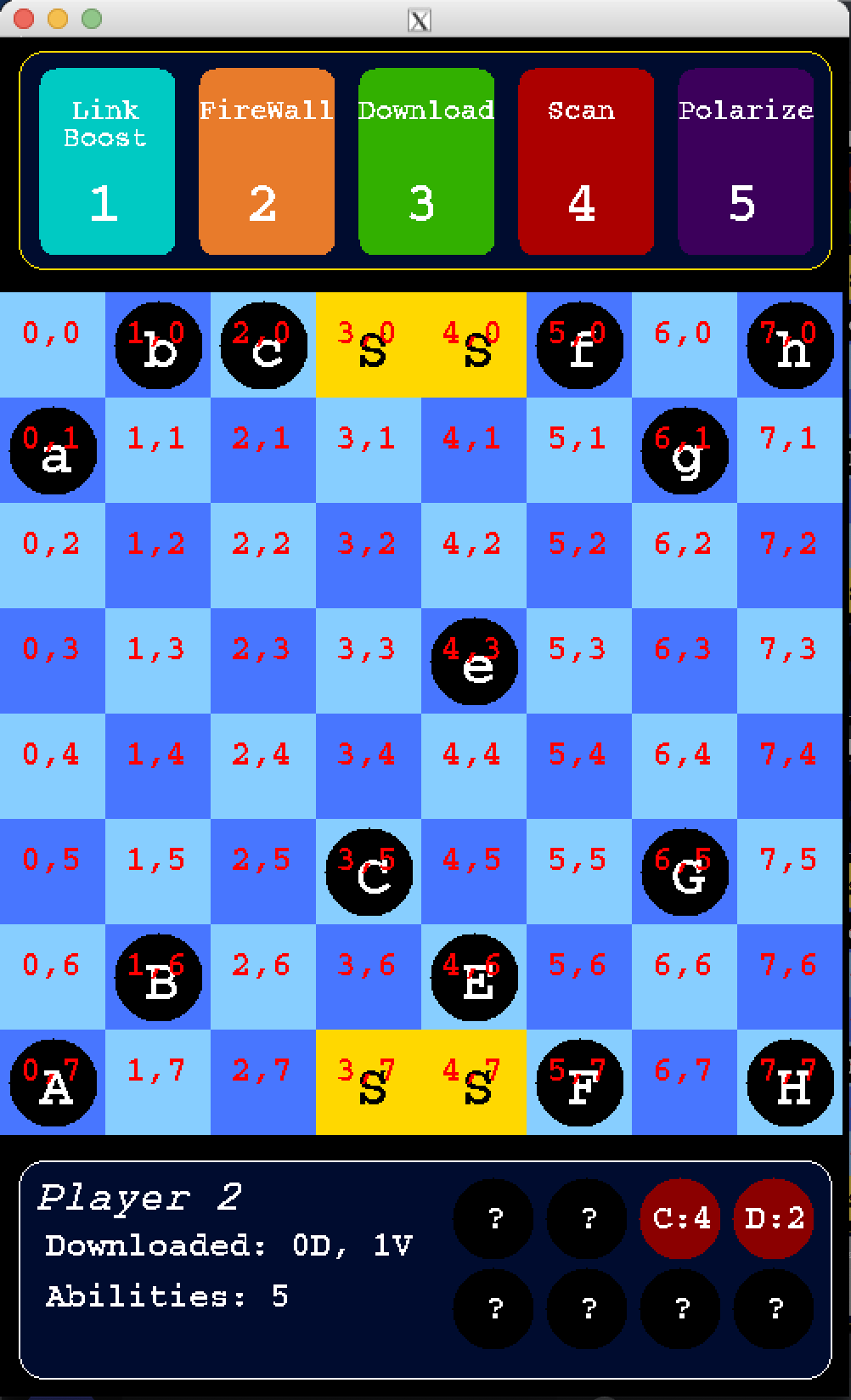
ByteBattles is a two-player strategy game where players assume the roles of computer hackers, controlling a set of links which are either viruses or data. The objective is to either download four pieces of data or make the opponent download four viruses.
- Technical Details
- Installation
- Gameplay
- Features
- Screenshots
- How to Play
- Commands
- Command Line Arguments
- License
- C++: The game is primarily developed in C++, leveraging its object-oriented capabilities for structured and efficient game design.
- Graphics Library: For the graphical interface, X11 is used, providing a robust platform for rendering the game elements and managing user interactions.
- Observer Pattern: Used for updating the graphical and text-based displays in response to changes in the game state.
- Factory Method: This pattern is utilized for creating different types of links (viruses and data) and abilities, allowing for easy extension and management.
- Model-View-Controller (MVC): MVC architecture separates the game logic (model) from the user interface (view), controlled by the game controller.
- Board Management: The game board is represented as a 2D grid, managing the placement and movement of links.
- Turn-Based System: We implemented a turn-based mechanism where each player has a set of actions they can perform per turn, including moving links and using abilities.
- Ability System: Abilities are modular and can be easily extended. Each ability class inherits from a common base, defining specific effects on the game state.
- Beautifully Crafted Game Assets: Our front-end was custom built and wireframed in Photoshop before being implemented.
For a more detailed understanding of ByteBattles's architecture and design considerations, please see the following documents:
- Design Document: A comprehensive guide detailing the design decisions, architecture, and the overall structure of the ByteBattles project.
- UML Diagram: The final UML diagram providing a visual overview of the system's classes, relationships, and design patterns.
These documents offer in-depth insights into our technical structure and development process of ByteBattles.
To install the game, follow these steps:
git clone https://github.com/yourgithubusername/ByteBattles.git
cd ByteBattles
# Follow platform-specific instructions to compile and run the gameByteBattles is played on an 8x8 board, with each player starting with 8 links - a mix of viruses and data. Players take turns to move their links and use special abilities, aiming to either download data or make their opponent download viruses. The game ends when a player achieves one of these objectives.
- Turn-Based Strategy: Engage in a strategic battle of wits with turn-based gameplay.
- Graphical & Text-Based UI: Play the game with a sleek graphical interface or a classic text-based view.
- Multiple Abilities: Utilize various abilities like Firewall, Download, and Polarize to gain an edge.
- Extensible Design: Easily add new abilities and features to the game.
ByteBattles is a strategy game that involves careful planning, strategic movement, and the use of special abilities. The game is played on an 8x8 grid, resembling a chessboard, with two players each controlling eight links. Here's a detailed guide on how to play the game:
- Board Setup: The game board is an 8x8 grid with the middle two squares on the first and last row designated as server ports.
- Choosing Links: Each player starts with 8 links - a mix of viruses and data, each having a strength between 1 and 4. Arrange your links on the first and last row of the board, avoiding placing them on the server ports.
- Selecting Abilities: Each player chooses five abilities from options like Link Boost, Firewall, Download, Scan, Polarize, Wall, and Backup. These abilities can be used strategically during the game.
The game proceeds in turns, with each player taking one turn at a time.
- Move a Link: On your turn, move one of your links one space in a cardinal direction (north, south, east, or west). You cannot move a link onto one of your own links or server ports. Moving a link will end your turn.
- Battle: If you move your link onto a space occupied by an opponent's link, a battle ensues. The link with the higher strength wins, and the loser's link is downloaded by the winner. In a tie, the attacking player wins.
- Download: Moving a link off the opponent's side of the board or into their server ports results in downloading that link.
- Use an Ability: You may use one of your abilities per turn, before moving a link. Abilities can change the game state significantly, like revealing link types or changing a link's allegiance.
Each ability adds a unique strategic element to the game. Here’s a breakdown:
- Effect: Enhances a link's mobility for one turn.
- Usage: Activate before moving a link.
- Strategic Tip: Ideal for quick positioning.
- Effect: Targets a square to reveal and potentially download opponent viruses.
- Usage: Place strategically on the board.
- Strategic Tip: Use to guard key areas.
- Effect: Instantly downloads an opponent’s link.
- Usage: Select an opponent's link.
- Strategic Tip: Target high-strength data links.
- Effect: Changes a link's type (data to virus or vice versa).
- Usage: Activate on a revealed link.
- Strategic Tip: Useful for deception or conversion.
- Effect: Reveals the type and strength of a link.
- Usage: Target an unrevealed link.
- Strategic Tip: Gain intelligence for strategy.
- Effect: Creates an impassable square.
- Usage: Activate to block paths or protect positions.
- Strategic Tip: Funnel opponent movements or create safe zones.
- Effect: Reverses a link's last move.
- Usage: Activate after a link moves.
- Strategic Tip: Correct mistakes or tactically retreat.
- Effect: Allows two link moves to be made.
- Usage: Activate at the start of the your turn before moving a link.
- Strategic Tip: Make big moves, bigger compounded with link boost.
The game ends when either:
- A player successfully downloads four data links, winning the game.
- A player is forced to download four virus links, resulting in their loss.
- Link Types: Keep in mind the types of links (virus or data) you're moving. Misleading your opponent can be a key strategy.
- Abilities: Use abilities wisely. They are limited and can turn the tide of the game.
- Positioning: Be strategic about the positioning of your links, especially when it comes to protecting your server ports and planning attacks.
Players can interact with the game using the following command line commands:
move <link> <direction>: Moves the specified link in the given direction (up,down,left,right).abilities: Displays the ability cards available to the player.ability <N>: Uses the ability card with ID N. May require additional information like a target or a board square.board: Displays the current state of the board.sequence <file>: Executes a sequence of commands from a specified file.quit: Exits the game.
When launching ByteBattles, you can customize your game setup using various command line arguments. Here’s a guide to using these options:
-
-ability1 <order>: Specifies the abilities for player 1. This is a list of the 5 abilities player 1 will use, given by a string consisting of the first letter of each ability. For example,-ability1 LFDSPfor Link boost, Firewall, Download, Scan, Polarize in that order. -
-ability2 <order>: Similar to-ability1, but for player 2. -
-link1 <placement-file>: Specifies the placement of links for player 1. The contents of<placement-file>should list what each link should be for player 1, in order fromatoh. For example, a file containingV1 D4 V3 V2 D3 V4 D2 D1sets up the links in the specified order. -
-link2 <placement-file>: As above, but for player 2. -
-graphics: Enables the graphical interface for the game. If this option is not specified, the game defaults to a text-based interface. -
-enablebonus: Enables bonus features.
Example usage:
./ByteBattles -ability1 LFDSP -ability2 DSPLF -link1 player1.txt -link2 player2.txt -graphicsThis command launches the game with specified abilities and link placements for both players and enables the graphical interface.
This project is licensed under the MIT License - see the LICENSE file for details.