MikrotikSploit is a script that searches for and exploits Mikrotik network vulnerabilities Loophole pull numbers of network login cards ... Loophole know the username and password of the admin panel of the network Mikrotik ... A special section of the DoS system
- Checks for vulnerabilities
- Integrated guess system on login cards
- Discover the name and password of the network management panel
- DDoS attack
- find the mistakes and resolve it
- Reporting: simple, Text.
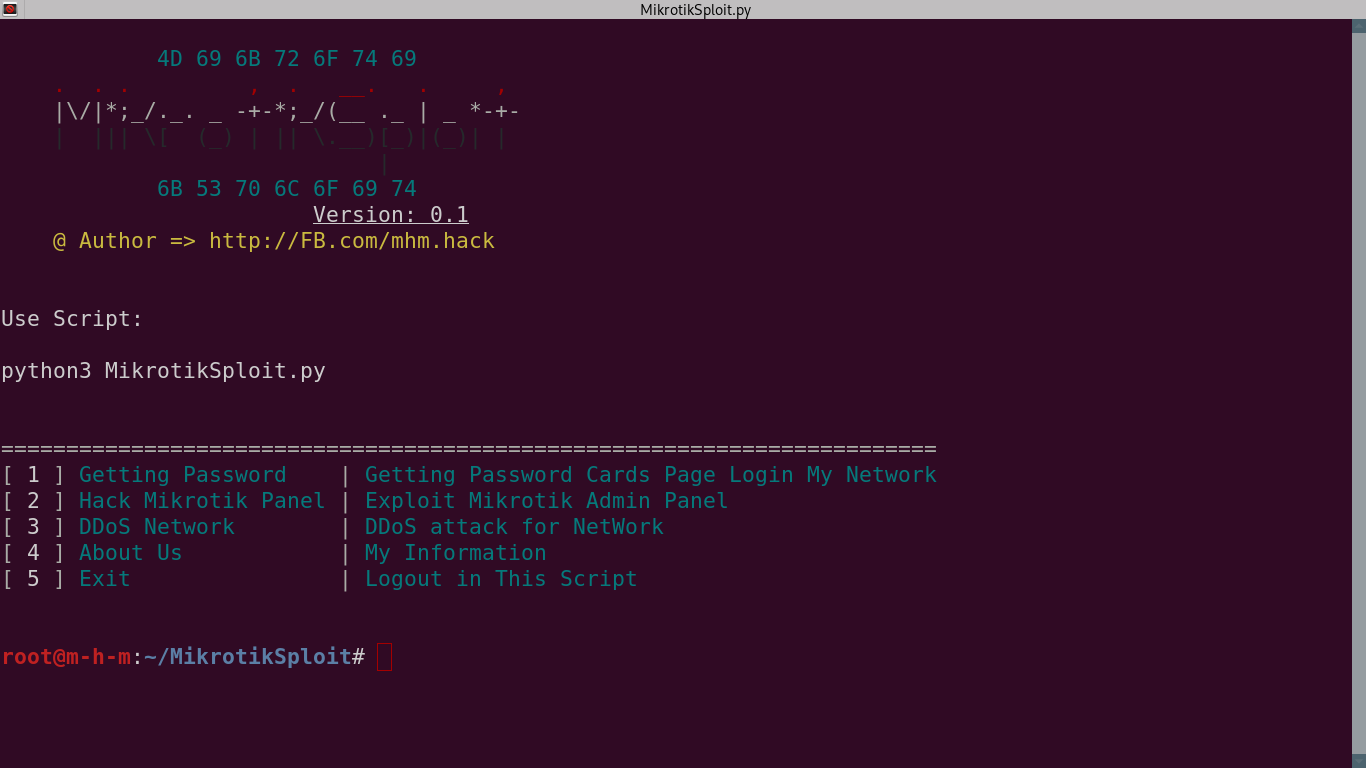
usage: MikrotikSploit [options]
[ 1 ] Getting Password | Getting Password Cards Page Login My Network
[ 2 ] Hack Mikrotik Panel | Exploit Mikrotik Admin Panel
[ 3 ] DoDs Network | DoDs for Your NetWork
[ 4 ] About Us | My Information
[ 5 ] Exit | Logout in This Script
MikrotikSploi in DOCKER !!.
$ git clone https://github.com/0x802/MikrotikSploit.git
$ cd MikrotikSploit
$ python3 -m pip install -r requirements.txt
$ python3 MikrotikSploit.py$ pkg update
$ pkg install -y git
$ git clone https://github.com/0x802/MikrotikSploit.git
$ cd MikrotikSploit
$ python3 -m pip install -r requirements.txt
$ python3 MikrotikSploit.py- click here to download MikrotikSploit
- download and install python3
- unzip MikrotikSploit-master.zip in c:/
- open the command prompt cmd.
> cd c:/MikrotikSploit-master
> py -m pip install -r requirements.txt
> py MikrotikSploit.py
- v0.1
I Am Not Responsible of any Illegal Use