The purpose of this repo is to outline the steps taken to setup an environment for Harbor.
Includes additional examples and discoveries while working on the demo.
Harbor is an open source cloud native registry that stores, signs, and scans container images for vulnerabilities.
Harbor solves common challenges by delivering trust, compliance, performance, and interoperability. It fills a gap for organizations and applications that cannot use a public or cloud-based registry, or want a consistent experience across clouds
Lighting Talk slides can be found here
It is recommended to install Harbor using Helm Charts, The latest chart can be found at goharbor/habor-helm
- K8s 1.8+ cluster
- K8s ingress controller enabled
- Helm and Tiller (with clusteradmin permissions) - this is for cert manager not harbor
- SSL certificates. (I used lets Encrypt cert-manager to accomplish this)
- setup storage (S3)
- clone harbor-helm repo
- update harbors helm values.yaml file with changes:
- externalDomain
- AdminPassword
- AuthenticationMode(local or LDAP)
- secretKey
- ingress core and notary domain
- ingress SecretName (for certificate)
- Storage for registry (s3)
- Install chart using custom values.yaml file
- Wait a few minutes before attempting to access the environment
*on first access the system will take time to start up with a "Loading..." screen, or a 502 Bad Gateway message, after about 10 minutes it will come up
Post Installtion Configuration steps:
- create users (if local)
- create projects (public or private)
- add members to projects
GKE work:
- setup lets encrypt (see GKE repo for notes)
install harbor:
helm install --debug --name demo -f demo-values.yaml .
to upgrade a release::
helm upgrade demo --debug -f demo-values.yaml .
setup:
- create user named
demo-adminanddemo-dev - create project named
demo-public(check public box) anddemo-private - add
demo-adminasProject Adminrole ondemo-publicproject - add
demo-devasDeveloperrole ondemo-privateproject
- login to docker:
docker login -u demo-admin harbor.domain.io - tag image:
docker tag msql:latest harbor.domain.io/demo-public/mysql:demo - push image:
docker push harbor.domain.io/demo-public/mysql:demo
- login to docker:
docker login -u demo-dev harbor.domain.io - tag image for private:
docker tag mysql:latest harbor.domain.io/demo-private/mysql:dev - push to private repo:
docker push harbor.domain.io/demo-private/mysql:dev
- open ui site: https://harbor.domain.io
- fill out form and username of
self-register - login with newly created account
- log into docker:
docker login -u self-register harbor.domain.io - pull public image:
docker pull harbor.domain.io/demo-public/mysql:demo - try and push to public repo:
docker push harbor.domain.io/demo-public/mysql:demo- results: shows access denied because
self-registeris not a member of thedemo-publicrepo.
- results: shows access denied because
- enable scan on push: configuration section of project
- run scan on image
- upload new image and see it get auto scanned
- install helm push plugin if not already installed
- add harbor to helm repo list:
helm repo add --username=demo-admin --password=REPLACEME harbor-demo-public https://harbor.domain.io/chartrepo/demo-public - make a helm package by creating by cloning a repo with helm chart ex: otter-api and from the cloned repo running
helm package charts/otter-api - push the package:
helm push --username=demo-admin --password=REPLACEME otter-api-0.1.0.tgz harbor-demo-public
*see harbor docs on manage-helm-charts
- create global label under configuration
- create project specific label under project > configuration
- run from a docker image using an alias:
alias harbor='docker run -e HARBOR_USERNAME="admin" -e HARBOR_PASSWORD="REPLACEME" -e HARBOR_PROJECT=1 -e HARBOR_URL="https://harbor.domain.io" --rm krystism/harborclient harbor' - create a user:
harbor user-create --username=cli-user --password=12345678 --email=cli-user@example.com
*It is useful for managing harbor via the cli for administration: users, projects, replication, configuration, logs, ect... Provides ways to automate the setup of harbor
**I am finding some commands are not working and it is limited on the management of users (not able to add a user to a project). Though the API does provide many options for automation as an alternative.
Links:
- https://github.com/goharbor/harbor/tree/master/contrib/harbor-cli
- https://github.com/int32bit/python-harborclient
- add new endpoint under "registries" of admin section
- choose replication schedule (immediant or scheduled)
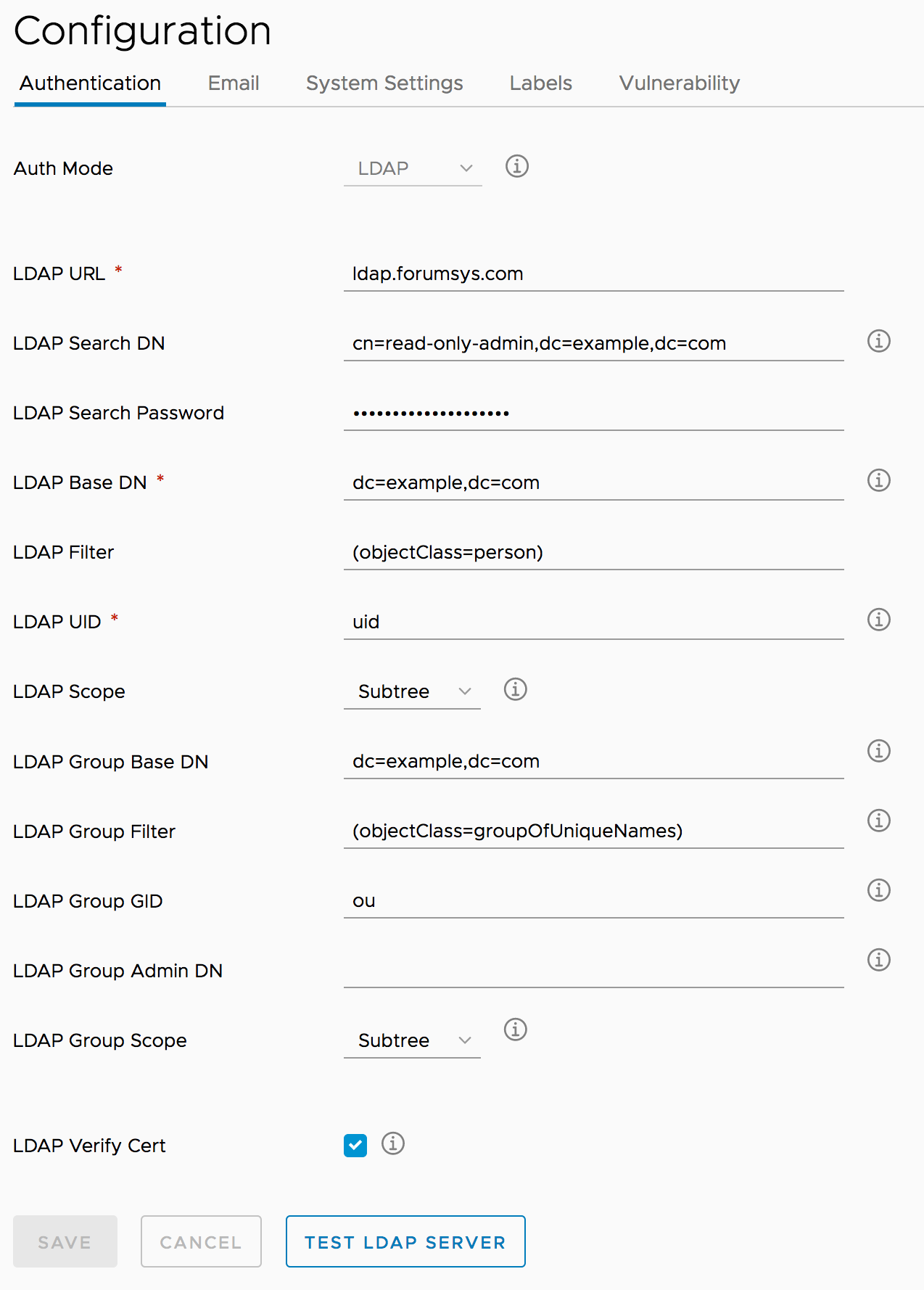
LDAP integration (using online LDAP test server)
- set ldap settings in values.yaml file for helm chart to include settings for ldap server.
- Example Authentication Settings:
Oauth2: Part of roadmap but work has not started yet: https://github.com/goharbor/harbor/blob/master/ROADMAP.md
Notary and signing
- https://github.com/goharbor/harbor/blob/master/docs/use_notary.md
- https://github.com/theupdateframework/notary
TODO:
Disaster Recovery:
- the database statefulset runs postgres and has a database called "registry" this appears to contains many of the settings for the harbor instance.
High Availability