This content is provided by the team at DoiT International, a global product and service organization dedicated to making the public cloud accessible while secure for all.
- Configure org policies
- Restrict allowed IAM domains
- Disable SA key creation
- Disable SA key upload
- Skip default network
- Disable external IPs
- Restrict prod networks to folder
- Require shielded VM
- Require OSLogin
- Require uniform bucket access
- Disable lein removal
- Prepare for VPC service controls (data protection)
- Create access policy (one per org)
- Disable org-level roles
- Billing admin
- Project creator
- Define disaster recovery plan
- DR team and contacts
- Geographical regions
- RTO, RPO
- Data backups
- Configuration management
- Continuous deployment
- Test schedule (at least annual)
- Establish user groups in GSuite / Cloud Identity
- Organization Admin
- Network Admin
- Security Admin
- Billing Admin
- Devops
- Developers
- Data Scientists
- Contractors
- Teams (project or folder-level as you grow)
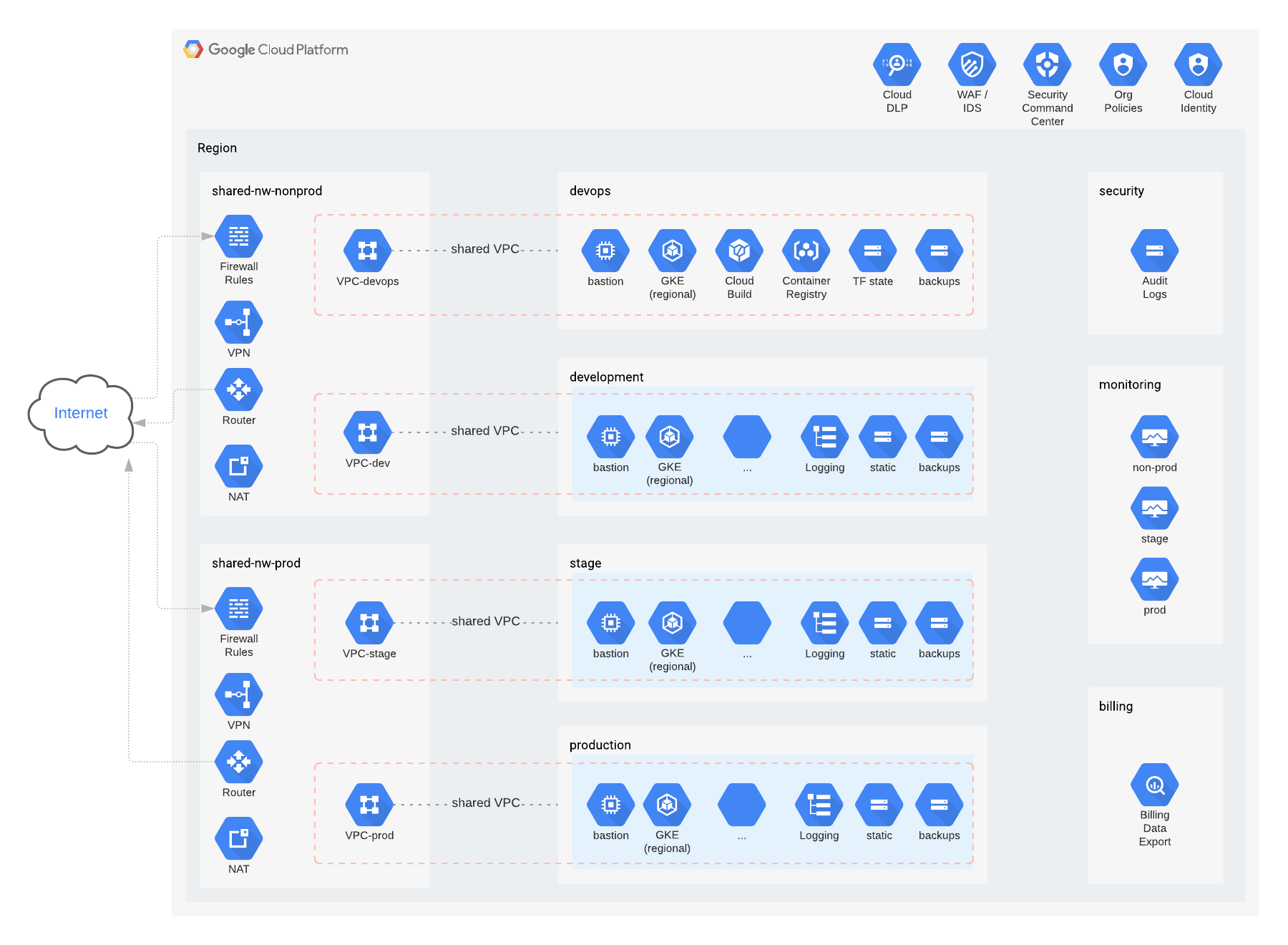
- Establish resource hierarchy
- Define folder and project hierarchy
- Define environment data security perimeters (VPC service controls)
- Set up IAM permissions
- Billing
- Org
- Folder
- Project
- Folder
- Tips:
- assign only groups IAM roles (not users)
- use
conditionswhere possible to limit access scope - set minimal permissions at each level as needed
- highest permission
Editorfor any project
- Set up Network
- Document IP address ranges (IPAM)
- Clusters
- secondary ranges
- VMs
- Databases
- Connectors
- Managed services
- Bastion (jump host)
- Clusters
- Create shared VPC (host project)
- VPCs
- Subnets
- Firewall rules
- Cloud Router
- NAT
- VPCs
- Serverless VPC Connector
- Document IP address ranges (IPAM)
- Set up Security project
- Enable audit logging at org level
- Create audit logging storage bucket
- Create aggregated audit log sinks to security project
- Set up Devops project
- Override key download policy (for this project)
- Create Terraform service account(s)
- Admin
- Developer (optional)
- Create artifact registry
- Service account permissions
- Container analysis
- Binary authorization
- Cloud Build
- Service account permissions
- Connect Git repositories
- Set up Billing project
- Create BigQuery dataset to store billing data
- Create billing export to bq dataset (only 1 per billing ID)
- Define resource labeling plan
- Set up Monitoring project
- Create initial workspace and add projects above
- Create logging bucket(s)
- Create notification channels
- Set up monitoring / alerts
- Billing / budget alerts
- CIS Benchmarks
- Add project leins to prevent accidental deletion (i.e. production)
- Audit log sink to
securityproject - Log sink to
monitoringproject logging bucket- Add exclusion filters or disable
_Default
- Add exclusion filters or disable
- Ensure network resources available
- Plan out or request network resources from shared VPC
- Add as service project
- Set up Service Accounts
- CI/CD
- Cache
- Database
- Storage
- App Runtime
- Add only permissions required for tasks
- OS Login
- Considerations:
- Storage bucket policy and lifecycle
- Data replications and RPO
- Data security perimeter
- Data loss prevention and PII
- Label resources
- Quotas
- Cloud IAP
- Firewall rules
- Monitoring
- Uptime checks
- Define SLO / SLI
- Dashboards
- Alerts
- Best practices for enterprise
- GCP for AWS professionals
- Identity best practices
- Inter-region latency and throughput
- Lowest-latency region check
- Creating organizations
- Migrating projects to org
- Migrating projects from org
- GSuite and Cloud Identity
- Enforce MFA login
- Service account keys best practices
- Log exports for compliance
- Log exclusion filters
- Centralize logs across projects
- Storage object lifecycles
- Monitoring and workspaces
- Request Annotation with logging
- Service monitoring (SLO/SLI)
- Disaster recovery
- Velero Kubernetes backups
- Project liens
- Labeling best practices
- Billing data exports
- VPC service controls
- Data loss prevention
- Remove PII from logs
- Compliance manager and audit reports
- Setting up budget alerts
- Budget alert notifications
- Automated resource scheduling (Zorya from DoiT)