- Public key is used to encrypt information.
- Private key is used to decrypt information.
- When encrypting, you(client) use their public key to write message, and they(server) use their private key to decrypt to read it.
- When signing, you(client) use your own private key to write message’s signature, and they(server) use your public key to verify if the message is yours.
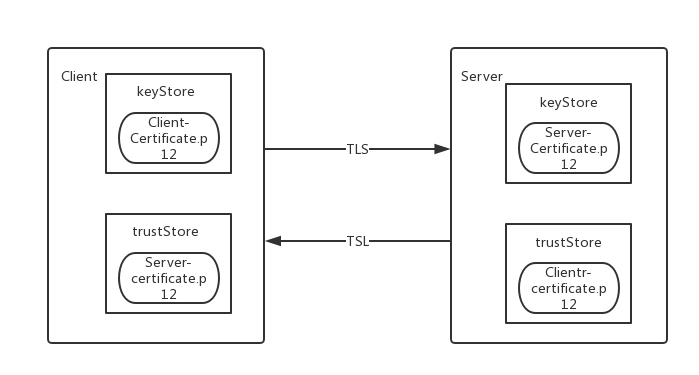
- A keystore has certs and keys in it and defines what is going to be presented to the other end of a connection.
- A truststore has just certs in it and defines what certs that the other end will send are to be trusted.
he standard SSL Handshake
- Client Hello (Information that the server needs to communicate with the client using SSL.)
- SSL version Number
- Cipher setting (Compression Method)
- Session-specific Data
- Server Hello
- Server picks a cipher and compression that both client and server support and tells the client about its choice, as well as some other things like a session id.
- Server presents its certificate ( This is what client needs to validate as being signed by a trusted CA.)
- Server presents a list of certificate authority DNs that client certs may be signed by.
- Client response
- Client continues the key exchange protocol necessary to set up a TLS session.
- Cclient presents a certificate that was signed by one of the CAs and encrypts with the server’s public key.
- Send the pre-master (based on cipher) encrypted by Server’s public key to server.
- Server accepts the cert presented by client.
- Server uses its private key to decrypt the pre-master secret. Both client and server perform steps to generate the master secret with the agreed cipher.
- Encryption with Session Key.
- Both client and server exchange messages to inform that future messages will be encrypted.
- Step 1. Create a private key and public certificate for client & server by openssl tool.
openssl req -newkey rsa:2048 -nodes -keyout client-key.pem -x509 -days 365 -out client-certificate.pemopenssl req -newkey rsa:2048 -nodes -keyout server-key.pem -x509 -days 365 -out server-certificate.pem- Step 2. Combine the private key and public certificate into
PCKS12(P12)format for client and server respectively.
openssl pkcs12 -inkey client-key.pem -in client-certificate.pem -export -out client-certificate.p12openssl pkcs12 -inkey server-key.pem -in server-certificate.pem -export -out server-certificate.p12-
Step 3. Place
client-certificate.p12andserver-certificate.p12intokeystoreandtrustStorelocation.