Issue POST Mihari > MISP with API
Celtic03 opened this issue · comments
Issue connecting Mihari results to MISP with API key
When running the mihari scripts the results are not being transfered to MISP instance with API.
I have tested the Mihari connection to MISP with API key and working with the following:
sudo curl -k -i -H "Accept: application/json" -H "content-type: application/json" -H "Authorization: MISP API KEY" --data "@TEST.json" https://MISPip/events/add
TEST.json;
{"Event":{"date":"2022-09-29","threat_level_id":"1","info":"testevent","published":false,"analysis":"0","distribution":"0","Attribute":[{"type":"domain","category":"Network activity","to_ids":false,"distribution":"0","comment":"","value":"test.com"}]}}
Mihari Script
title: EXAMPLE - dnstwister
description: Typosquatting
allowed_data_types: # Array (Optional, defaults to ["hash", "ip", "domain", "url", "mail"])
disallowed_data_values: [] # Array (Optional, defaults to [])
ignore_old_artifacts: true # Whether to ignore old artifacts from checking or not (Optional, defaults to true)
ignore_threshold: 30 # Number of days to define whether an artifact is old or not (Optional, defaults to 0)
queries: # Array (required)
- analyzer: dnstwister # String (required)
query: EXAMPLE.com
emitters:
- emitter: misp
api_endpoint: MISP_API_ENDPOINT=MISPip
api_key: MISP_API_KEY=MISP API Key
id: EXAMPLE - dnsTwist # String (optional)
author: # String (optional)
Converted Mihari Script to .JSON File
I have also converted the resultes of the mihari script to test.json file
used the following commend to upload the file;
sudo curl -k -i -H "Accept: application/json" -H "content-type: application/json" -H "Authorization: MISP API KEY" --data "@TEST2.json" https://MISPip/events/add
i recieve the following;
HTTP/1.1 405 Method Not Allowed
Date: Tue, 04 Oct 2022 10:17:49 GMT
Server: Apache/2.4.41 (Ubuntu)
Strict-Transport-Security: max-age=31536000; includeSubdomains;
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Upgrade: h2
Connection: Upgrade
Set-Cookie: MISP--422b-9ec8-e3664a8dcf97=prdcvkgdunlh6tneoo0vnhk462gjh7gf; expires=Thu, 06-Oct-2022 22:17:49 GMT; Max-Age=216000; path=/; secure; HttpOnly; SameSite=Lax
Set-Cookie: MISP-422b-9ec8-e3664a8dcf97=prdcvkgdunlh6tneoo0vnhk462gjh7gf; expires=Thu, 06-Oct-2022 22:17:49 GMT; Max-Age=216000; path=/; secure; HttpOnly; SameSite=Lax
Set-Cookie: MISP-422b-9ec8-e3664a8dcf97=0anvj9jdpevs9cme9jlripjcqiek3rck; expires=Thu, 06-Oct-2022 22:17:49 GMT; Max-Age=216000; path=/; secure; HttpOnly; SameSite=Lax
Set-Cookie: MISP--422b-9ec8-e3664a8dcf97=0anvj9jdpevs9cme9jlripjcqiek3rck; expires=Thu, 06-Oct-2022 22:17:49 GMT; Max-Age=216000; path=/; secure; HttpOnly; SameSite=Lax
Expires: Mon, 26 Jul 1997 05:00:00 GMT
Last-Modified: Tue, 04 Oct 2022 10:17:49 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
X-Username: admin@admin.test/API/1
Content-Length: 344
Content-Type: application/json; charset=UTF-8
{"name":"Invalid JSON input. Make sure that the JSON input is a correctly formatted JSON string. This request has been blocked to avoid an unfiltered request.","message":"Invalid JSON input. Make sure that the JSON input is a correctly formatted JSON string. This request has been blocked to avoid an unfiltered request.","url":"/events/add"}
Unsure of what i am doing wrong.
Mihari output (= Mihari alert JSON data) is not compatible with the MISP event format.
Mihari converts an alert into a MISP event and sends it to a MISP server.
Your report is difficult to read and so I'm not 100% sure but I cannot reproduce the issue.
Mihari (v4.9.0) works along with MISP v2.4.159.
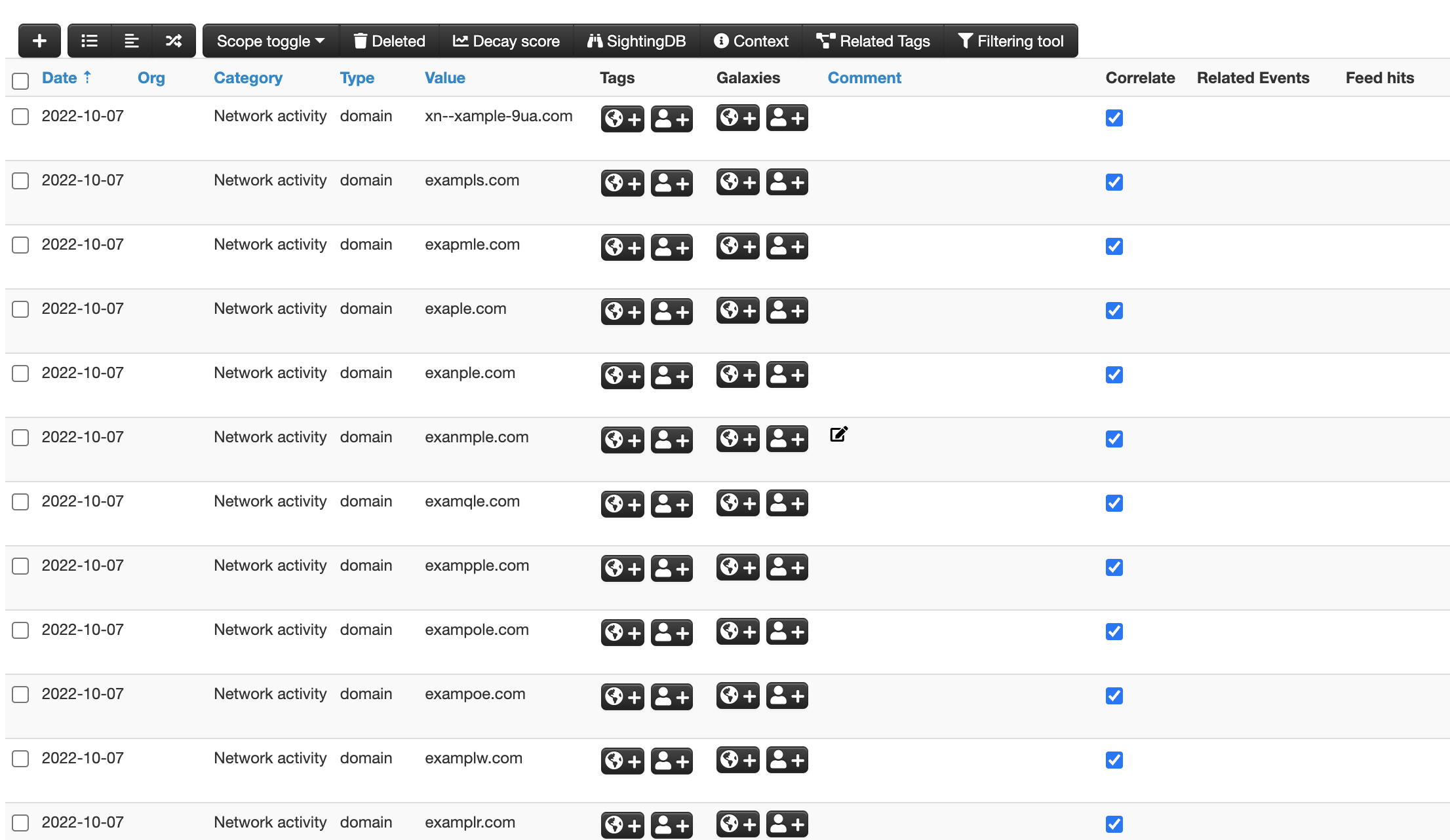
The following is a screenshot of a MISP event created by the DNSTwister query.
One possible cause is you set MISP_API_ENDPOINT (api_endpoint) in a wrong form.
It should be a full URL like http://localhost.
Also please follow the bug report format next time.