A collection of tools to enumerate and analyse Windows DACLs
Released as open source by NCC Group Plc - http://www.nccgroup.com/
Developed by Ollie Whitehouse, ollie dot whitehouse at nccgroup dot com
https://github.com/nccgroup/WindowsDACLEnumProject
Released under AGPL see LICENSE for more information
Read - http://msdn.microsoft.com/en-us/library/windows/desktop/aa446597(v=vs.85).aspx
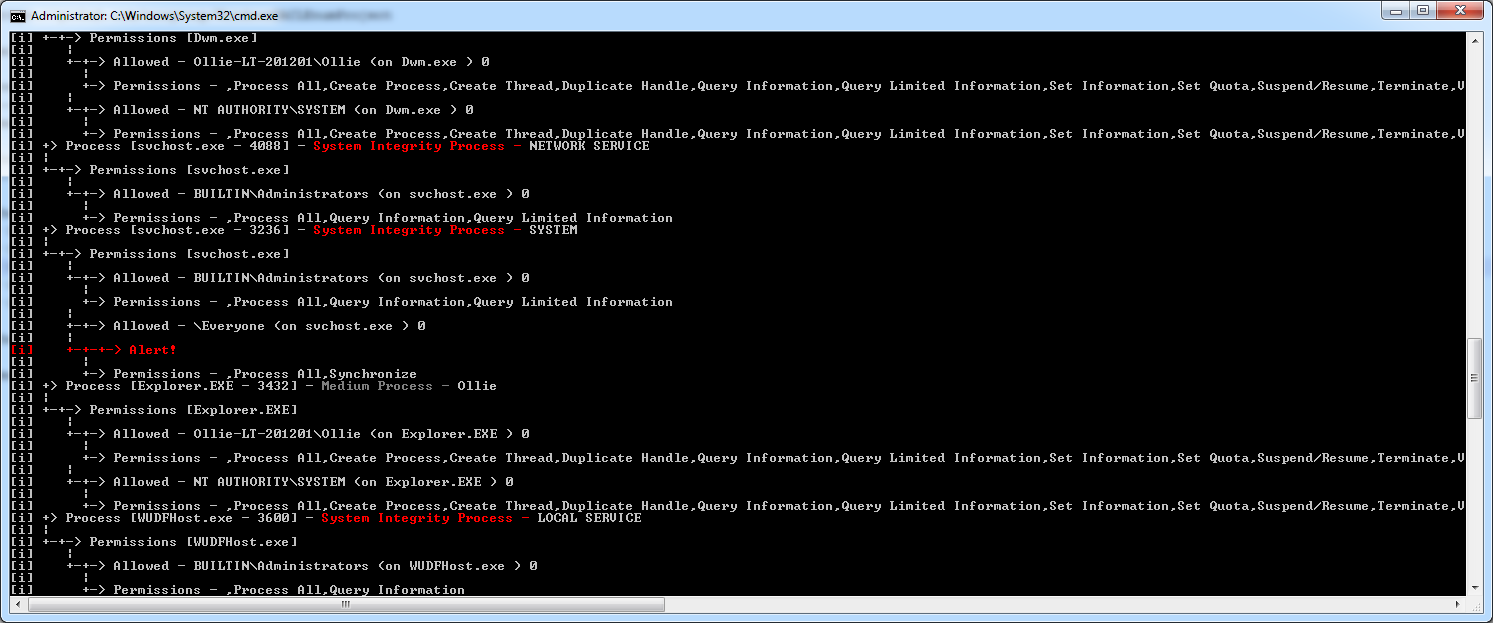
The first tool released as part of this project. Will enumerate:
- Processes and the integrity level and user they are running as.
- Optionally: the DACLs associated with the process object.
- Optionally: the threads for a process and the DACLs associated with them.
- Optionally: The modules loaded by a process
- Optionally: Exclude non mapped SIDs from the output
The tool will automatically flag any suspicious DACLs.
The command line take the following options:
- -p Process permissions
- -m Modules
- -t Threads and permissions
- -o [PID]
- -x exclude non mapped SIDs from alerts
Typical usage will be with a command line such as: processperms -px
The tool is designed for Windows Vista / Server 2008 and higher due to integrity level awareness.
======= Designed for Windows Vista / Server 2008 and higher due to integrity level awareness.
The second tool released as part of this project. Will enumerate:
- Window Stations within the session that it is executed and the associated DACL
- Desktops within those Window Stations and the associated DACLs
The third tool released as part of this project. Will enumerate:
- Services including kernel drivers, filter drivers and user land services.
- DACLs associated with the service entries in the service control manager.
- Service status, PID, binary path.
- DACLs associated with with the binaries associated
- Flag obviously weak DACLs
The fourth tool released as part of this project. Will enumerate:
- Files and access control lists
- Directories and access control lists
- Alert on files or directories with access control which appear weak
The fifth tool released as part of this project. Will enumerate:
- Registry keys and access control lists
- Alert on keys with access control which appear weak
- -s parameter to exclude all but the most suspicious output (see -h).
- -x paramater to only alert on suspicious output (see -h).