Why is the first part of encrypted text always the same? I still know of NO GOOD reason and I've been watching for *years*. There's something FISHY here.
firepacket opened this issue · comments
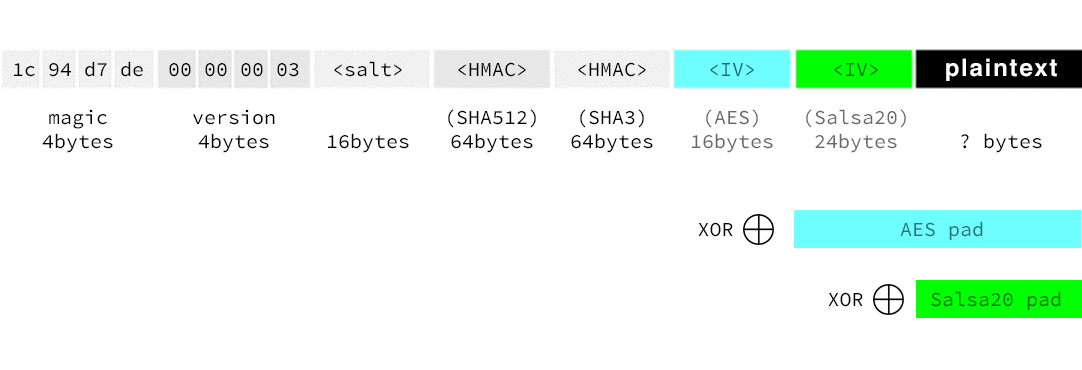
What are MAGIC BYTES?
They've been the same forever and haven't changed. Have you ever actually explained what they mean? What's their significance? They aren't encrypted, so the main annoyance is all our cipher text is immediacy identifiable as Triplesec encryption. And it wastes space.
4 bytes for the version?
Excuse me, you have 255 vales in a single byte. Yet you need 4 of them?
Has ANYONE heard a good explanation for this crap? I've been watching this project with love for years waiting for it to "click" and make sense.
It doesn't make sense. No other encryption suite would do this.
I do use Triplesec, but if anyone could actually SEE multiple cipher texts, there's no way. It looks unprofessional to to have repeating characters over and over... THEN THEY WILL QUESTION YOUR COMPETENCE FOR WASTING SPACE.
There's a million ways to do this, so why do it like this?
The only thing I can think of is that it's a highly noticeable degrading indicator when using Triplesec. But why put such an obvious indicator in your security product unless you are trying to communicate something? And why make it so annoying and unbeneficial?
What is this crap? What are the Magic Bytes? Please tell me. You've been hand-waving it away for almost a decade.
The magic bytes are used in order for the software to know that the file that you try to decrypt follow the triplesec format. As far as I know, they have no other meaning. It is very common for software to have a magic marker. You could find some information about magic markers on a Wikipedia article: https://en.wikipedia.org/wiki/File_format#Magic_number
PNG files start with eight bytes including "PNG" https://en.wikipedia.org/wiki/Portable_Network_Graphics#File_header
PDF files start with "%PDF" https://en.wikipedia.org/wiki/PDF#File_format
If you don't need compatibility with the default triplesec client and prefer removing the header, you could just remove the eight first bytes yourself and readd it before decrypting. You could fork the project and remove the header by editing the source code. You could also use a script to edit the files or edit them manually.
The magic bytes are used in order for the software to know that the file that you try to decrypt follow the triplesec format. As far as I know, they have no other meaning.
So you're telling me they are ARBITRARY? That doesn't raise red flags to anyone in the security field? FOUR WHOLE BYTES with NO EXPLANATION. That is by the stupidest thing I've ever heard. FOUR BYTES? Couldn't they make do with 1 for version? Why do you need ANYTHING "ARBITRARY" if you have a version byte and a structured format. This is what EVERY OTHER SECURITY FORMAT DOES.
You don't even need ANY bytes, you can just attempt the parse the structure. Lots of security software does this too.
Where are the Block Ciphers with arbitrary bytes? Where are the KDF functions with arbitrary bytes? NOBODY DOES THIS. It's ridiculous. YOU ARE HIDING SOMETHING. Wasting our precious space in all our cipher texts without offering any explanation. How many gigabytes of data do you think are wasted in databases all around the world storing multiple copies of these 8 useless bytes?
It is very common for software to have a magic marker.
NO IT'S NOT!!
NOT WITH ENCRYPTION WHERE EVERY VALUE IS VETTED FOR JUSTIFIED PURPOSE. This is a huge red flag and I would encourage people to do their own homework on what this type of poor security practice might mean.
"MAGIC BYTES" are not ARBITRARY. They are there for a reason which you aren't aware of or are unwilling to discuss. This is obvious deception.
PNG files start with eight bytes including "PNG" https://en.wikipedia.org/wiki/Portable_Network_Graphics#File_header
PDF files start with "%PDF" https://en.wikipedia.org/wiki/PDF#File_format
FILE FORMATS are not ENCRYPTION SCHEMES. This is childish reasoning, comparing apples to oranges. For all I know those 4 magic bytes offer some unknown weakness into the algorithm. If you can't explain your reasoning as to what those values mean, then you're HIDING SOMETHING.. You can't pretend they mean nothing.
If you don't need compatibility with the default triplesec client and prefer removing the header, you could just remove the eight first bytes yourself and readd it before decrypting. You could fork the project and remove the header by editing the source code. You could also use a script to edit the files or edit them manually.
Yes I sure could, but I wouldn't waste my time unless I understood what they are DOING THERE in the first place. WHY are they there, and if forking and removing them would even fix the problem.
It's a baffling mystery and I posit that this is CLEAR UNDENIABLE EVIDENCE that there is something scandalous going on with "Triplesec" we do not understand.