Add function for AES encryption to sdk
mikhailUshakoff opened this issue · comments
Popular AES Encryption is missing in current crypto module implementation.
AES Encryption should support:
- 128-bit, 192-bit and 256-bit key sizes.
- CBC, CFB, CTR, ECB and OFB modes.
The Electronic Codebook Mode (ECB)
The Electronic Codebook (ECB) mode is a confidentiality mode that features, for a given key,
the assignment of a fixed ciphertext block to each plaintext block, analogous to the assignment of
code words in a codebook. The Electronic Codebook (ECB) mode is defined as follows:
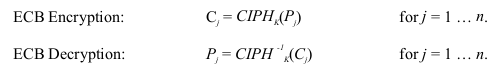
In ECB encryption, the forward cipher function is applied directly and independently to each
block of the plaintext. The resulting sequence of output blocks is the ciphertext.
In ECB decryption, the inverse cipher function is applied directly and independently to each
block of the ciphertext. The resulting sequence of output blocks is the plaintext.
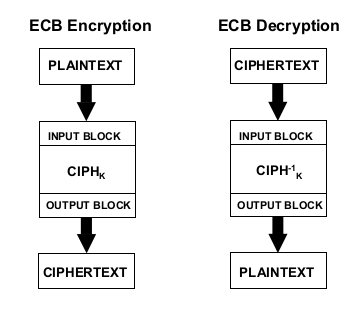
In ECB encryption and ECB decryption, multiple forward cipher functions and inverse cipher
functions can be computed in parallel.
In the ECB mode, under a given key, any given plaintext block always gets encrypted to the
9same ciphertext block. If this property is undesirable in a particular application, the ECB mode
should not be used.
The Cipher Block Chaining Mode (CBC)
The Cipher Block Chaining (CBC) mode is a confidentiality mode whose encryption process
features the combining (“chaining”) of the plaintext blocks with the previous ciphertext blocks.
The CBC mode requires an IV to combine with the first plaintext block. The IV need not be
secret, but it must be unpredictable; the generation of such IVs is discussed in Appendix C.
Also, the integrity of the IV should be protected, as discussed in Appendix D. The CBC mode is
defined as follows:
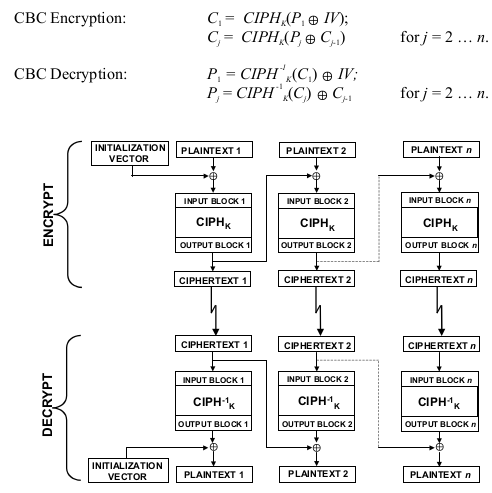
In CBC encryption, the first input block is formed by exclusive-ORing the first block of the
plaintext with the IV. The forward cipher function is applied to the first input block, and the
resulting output block is the first block of the ciphertext. This output block is also exclusive-
ORed with the second plaintext data block to produce the second input block, and the forward
cipher function is applied to produce the second output block. This output block, which is the
second ciphertext block, is exclusive-ORed with the next plaintext block to form the next input
block. Each successive plaintext block is exclusive-ORed with the previous output/ciphertext
block to produce the new input block. The forward cipher function is applied to each input block
to produce the ciphertext block.
In CBC decryption, the inverse cipher function is applied to the first ciphertext block, and the
resulting output block is exclusive-ORed with the initialization vector to recover the first
plaintext block. The inverse cipher function is also applied to the second ciphertext block, and
the resulting output block is exclusive-ORed with the first ciphertext block to recover the second
plaintext block. In general, to recover any plaintext block (except the first), the inverse cipher
function is applied to the corresponding ciphertext block, and the resulting block is exclusive-
ORed with the previous ciphertext block.
In CBC encryption, the input block to each forward cipher operation (except the first) depends on
the result of the previous forward cipher operation, so the forward cipher operations cannot be
performed in parallel. In CBC decryption, however, the input blocks for the inverse cipher
function, i.e., the ciphertext blocks, are immediately available, so that multiple inverse cipher
operations can be performed in parallel.
The Cipher Feedback Mode (CFB)
The Cipher Feedback (CFB) mode is a confidentiality mode that features the feedback of
successive ciphertext segments into the input blocks of the forward cipher to generate output
blocks that are exclusive-ORed with the plaintext to produce the ciphertext, and vice versa. The
CFB mode requires an IV as the initial input block. The IV need not be secret, but it must be
unpredictable; the generation of such IVs is discussed in Appendix C.
The CFB mode also requires an integer parameter, denoted s, such that 1 ≤ s ≤ b. In the
specification of the CFB mode below, each plaintext segment (P j ) and ciphertext segment (C j )
consists of s bits. The value of s is sometimes incorporated into the name of the mode, e.g., the
1-bit CFB mode, the 8-bit CFB mode, the 64-bit CFB mode, or the 128-bit CFB mode.
The CFB mode is defined as follows:
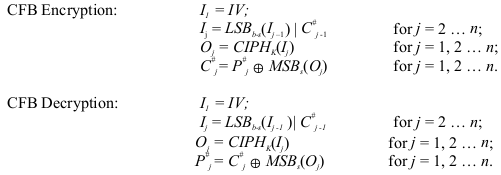
In CFB encryption, the first input block is the IV, and the forward cipher operation is applied to
the IV to produce the first output block. The first ciphertext segment is produced by exclusive-
ORing the first plaintext segment with the s most significant bits of the first output block. (The
remaining b-s bits of the first output block are discarded.) The b-s least significant bits of the IV
are then concatenated with the s bits of the first ciphertext segment to form the second input
block. An alternative description of the formation of the second input block is that the bits of
the first input block circularly shift s positions to the left, and then the ciphertext segment
replaces the s least significant bits of the result.
The process is repeated with the successive input blocks until a ciphertext segment is produced
from every plaintext segment. In general, each successive input block is enciphered to produce
an output block. The s most significant bits of each output block are exclusive-ORed with the
corresponding plaintext segment to form a ciphertext segment. Each ciphertext segment (except
the last one) is “fed back” into the previous input block, as described above, to form a new input
block.
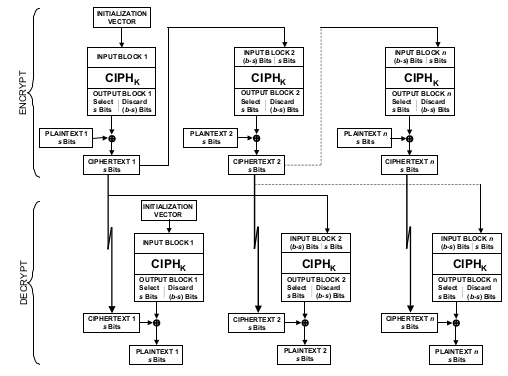
In CFB decryption, the IV is the first input block, and each successive input block is formed as in
CFB encryption, by concatenating the b-s least significant bits of the previous input block with
the s most significant bits of the previous ciphertext. The forward cipher function is applied to
each input block to produce the output blocks. The s most significant bits of the output blocks
are exclusive-ORed with the corresponding ciphertext segments to recover the plaintext
segments.
In CFB encryption, like CBC encryption, the input block to each forward cipher function (except
the first) depends on the result of the previous forward cipher function; therefore, multiple
forward cipher operations cannot be performed in parallel. In CFB decryption, the required
forward cipher operations can be performed in parallel if the input blocks are first constructed (in
series) from the IV and the ciphertext.
The Output Feedback Mode (OFB)
The Output Feedback (OFB) mode is a confidentiality mode that features the iteration of the
forward cipher on an IV to generate a sequence of output blocks that are exclusive-ORed with
the plaintext to produce the ciphertext, and vice versa. The OFB mode requires that the IV is a
nonce, i.e., the IV must be unique for each execution of the mode under the given key; the
generation of such IVs is discussed in Appendix C. The OFB mode is defined as follows:
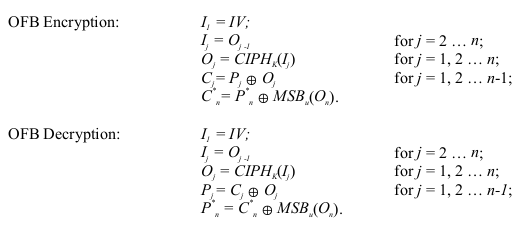
In OFB encryption, the IV is transformed by the forward cipher function to produce the first
output block. The first output block is exclusive-ORed with the first plaintext block to produce
the first ciphertext block. The forward cipher function is then invoked on the first output block
to produce the second output block. The second output block is exclusive-ORed with the second
plaintext block to produce the second ciphertext block, and the forward cipher function is
invoked on the second output block to produce the third output block. Thus, the successive
output blocks are produced from applying the forward cipher function to the previous output
blocks, and the output blocks are exclusive-ORed with the corresponding plaintext blocks to
produce the ciphertext blocks. For the last block, which may be a partial block of u bits, the
most significant u bits of the last output block are used for the exclusive-OR operation; the
remaining b-u bits of the last output block are discarded.
In OFB decryption, the IV is transformed by the forward cipher function to produce the first
output block. The first output block is exclusive-ORed with the first ciphertext block to recover
the first plaintext block. The first output block is then transformed by the forward cipher
function to produce the second output block. The second output block is exclusive-ORed with
the second ciphertext block to produce the second plaintext block, and the second output block is
also transformed by the forward cipher function to produce the third output block. Thus, the
successive output blocks are produced from applying the forward cipher function to the previous
output blocks, and the output blocks are exclusive-ORed with the corresponding ciphertext
blocks to recover the plaintext blocks. For the last block, which may be a partial block of u bits,
the most significant u bits of the last output block are used for the exclusive-OR operation; the
remaining b-u bits of the last output block are discarded.
In both OFB encryption and OFB decryption, each forward cipher function (except the first)
depends on the results of the previous forward cipher function; therefore, multiple forward cipher
functions cannot be performed in parallel. However, if the IV is known, the output blocks can be
generated prior to the availability of the plaintext or ciphertext data.
The OFB mode requires a unique IV for every message that is ever encrypted under the given
key. If, contrary to this requirement, the same IV is used for the encryption of more than one
message, then the confidentiality of those messages may be compromised. In particular, if a
plaintext block of any of these messages is known, say, the jth plaintext block, then the jth output
of the forward cipher function can be determined easily from the jth ciphertext block of the
message. This information allows the jth plaintext block of any other message that is encrypted
using the same IV to be easily recovered from the jth ciphertext block of that message.
Confidentiality may similarly be compromised if any of the input blocks to the forward cipher
function for the encryption of a message is designated as the IV for the encryption of another
message under the given key.
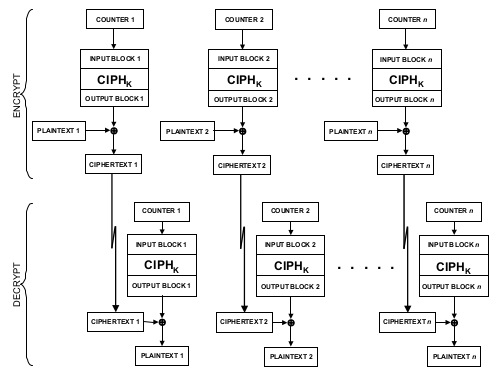
The Counter Mode (CTR)
The Counter (CTR) mode is a confidentiality mode that features the application of the forward
cipher to a set of input blocks, called counters, to produce a sequence of output blocks that are
exclusive-ORed with the plaintext to produce the ciphertext, and vice versa. The sequence of
counters must have the property that each block in the sequence is different from every other
block. This condition is not restricted to a single message: across all of the messages that are
encrypted under the given key, all of the counters must be distinct. In this recommendation, the
counters for a given message are denoted T 1 , T 2 , ... , T n . Methods for generating counters are
discussed in Appendix B. Given a sequence of counters, T 1 , T 2 , ... , T n , the CTR mode is
defined as follows:
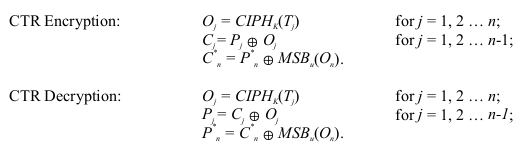
In CTR encryption, the forward cipher function is invoked on each counter block, and the
resulting output blocks are exclusive-ORed with the corresponding plaintext blocks to produce
the ciphertext blocks. For the last block, which may be a partial block of u bits, the most
significant u bits of the last output block are used for the exclusive-OR operation; the remaining
b-u bits of the last output block are discarded.
In CTR decryption, the forward cipher function is invoked on each counter block, and the
resulting output blocks are exclusive-ORed with the corresponding ciphertext blocks to recover
the plaintext blocks. For the last block, which may be a partial block of u bits, the most
significant u bits of the last output block are used for the exclusive-OR operation; the remaining
b-u bits of the last output block are discarded.
In both CTR encryption and CTR decryption, the forward cipher functions can be performed in
parallel; similarly, the plaintext block that corresponds to any particular ciphertext block can be
recovered independently from the other plaintext blocks if the corresponding counter block can
be determined. Moreover, the forward cipher functions can be applied to the counters prior to the
availability of the plaintext or ciphertext data.