Could not connect with self sign certificate of elasticsearch
aaryabhatt opened this issue · comments
Hi,
I tried to connect to a elasticsearch in openshft aggregate logging with self sign certificate. It is not connecting. I tried to connect with curl, it work with -k option to bypass the verification of certificate. If I try without -k option than it give the ssl verification error.
see this.
`root@logging-elastalert:/var/www/411# curl -XGET -k --cert cert "https://logging-es:9200/"
{
"name" : "logging-es-data-master-0v7g47an",
"cluster_name" : "logging-es",
"cluster_uuid" : "BRhd6zhNSGCg9SR7JZRSeQ",
"version" : {
"number" : "2.4.4",
"build_hash" : "fcbb46dfd45562a9cf00c604b30849a6dec6b017",
"build_timestamp" : "2017-01-03T11:33:16Z",
"build_snapshot" : false,
"lucene_version" : "5.5.2"
},
"tagline" : "You Know, for Search"
}
root@logging-elastalert:/var/www/411# curl -XGET --cert cert "https://logging-es:9200/"
curl: (60) SSL certificate problem: self signed certificate in certificate chain
More details here: https://curl.haxx.se/docs/sslcerts.html
curl performs SSL certificate verification by default, using a "bundle"
of Certificate Authority (CA) public keys (CA certs). If the default
bundle file isn't adequate, you can specify an alternate file
using the --cacert option.
If this HTTPS server uses a certificate signed by a CA represented in
the bundle, the certificate verification probably failed due to a
problem with the certificate (it might be expired, or the name might
not match the domain name in the URL).
If you'd like to turn off curl's verification of the certificate, use
the -k (or --insecure) option.
`
I got the below error.
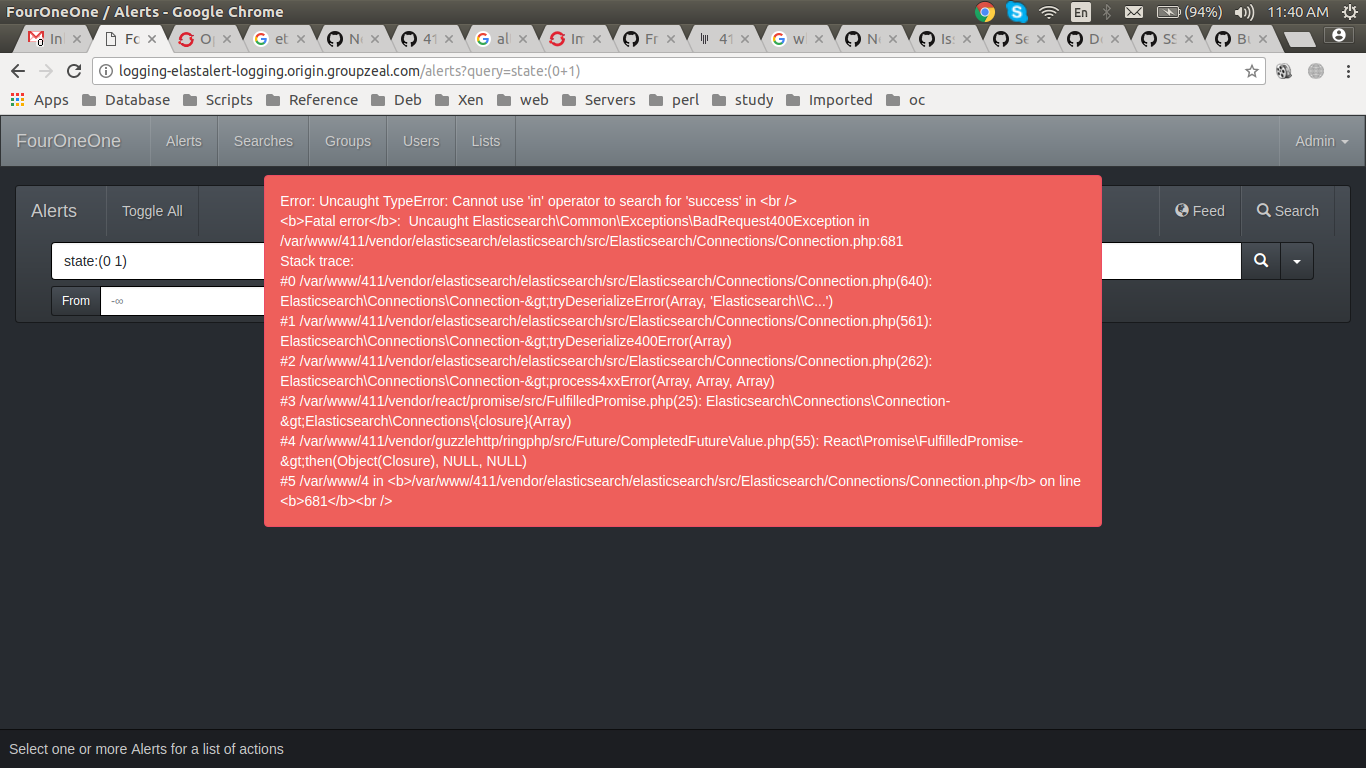
my config.php setting are:-
# Configuration for the 411 Alerts index. 'alerts' => [ 'hosts' => ['https://logging-es:9200'], 'index_hosts' => [], 'ssl_cert' => "/var/www/411/cert", //'ssl_cert' => null, 'index' => null, 'date_based' => false, 'date_interval' => null, 'date_field' => 'alert_date', 'date_type' => null, 'src_url' => null, ], # Configuration for the logstash index that 411 queries. 'operation' => [ 'hosts' => ['https://logging-es:9200'], 'index_hosts' => [], // 'ssl_cert' => null, 'ssl_cert' => "/var/www/411/cert", 'index' => '[.operations.]Y.m.d', 'date_based' => false, 'date_interval' => 'd', 'date_field' => '@timestamp', 'date_type' => null, 'src_url' => null, ],
How I can use ssl not verify option in setting of config.php.
Thanks.
Do you have a copy of the certificate? Passing it in the ssl_cert option should do the job.
Hi Kiwiz, Thanks for your reply. I have this SSl certificate. As I mentioned that I can access access it through CURL and if the certificate was not proper earlier, it was giving error something like bundle CA not found in elasticsearch logs. Now it don't show any logs at elasticsearch.
I am trying to access a elasticsearch server deployed by EFK aggregate logging in openshift origin 3.5.
Which used the key based authentication for elasticsearch.
So I made a bundle certificate of secret in a single file in order cert + key + ca. I tried to use the different user secret certificate but still the same issue. I also tried to use older version of etsy/411 1.3 but it is still the same issue. I am getting the same error shown in image. If you will see config.php setting above, it is using ssl_cert option with full path of cert file.
Is there any method by which I can check the connectivity to elasticsearch from 411 app and trace the logs?
The relevant line is here: https://github.com/etsy/411/blob/master/phplib/Search/Elasticsearch.php#L153, via setSSLVerification. Can you test your bundle with a minimal script?
This link might also help: https://www.elastic.co/guide/en/elasticsearch/client/php-api/current/_security.html.
Thanks Kiwiz, apologize for late response. I don't have knowledge of php and try to search a lot of docs ut little confused to used.
I tried the bundle cert with curl and it works fine from same container. It would be great help if you can help me set this test script environment in that container.
root@logging-elastalert:/var/www/411# curl -XGET -k --cert cert.pem "https://logging-es:9200/_cat/indices?v" health status index pri rep docs.count docs.deleted store.size pri.store.size green open elastalert_status 1 0 0 0 159b 159b green open .operations.2017.12.06 1 0 22216489 0 6.3gb 6.3gb green open .operations.2017.12.05 1 0 22132281 0 6.3gb 6.3gb green open .operations.2017.12.08 1 0 22186730 0 6.3gb 6.3gb green open .operations.2017.12.07 1 0 22122240 0 6.3gb 6.3gb green open .searchguard.logging-es-data-master-0v7g47an 1 0 5 0 33kb 33kb
HI Kiwiz, I tried to build a test script to test connectivity but still getting the same error.
my php script
<?php
require 'vendor/autoload.php';
$hosts = ['https://logging-es:9200'];
$myCert = '/var/www/411/cert.pem';
$client = Elasticsearch\ClientBuilder::create()
->setHosts($hosts)
->setSSLVerification($myCert)
->build();
$params = [
'index' => '.operations.2017.12.06',
'type' => 'com.redhat.viaq.common',
'id' => 'AWAqLKx4unTnyFKFOn8j'
];
$response = $client->get($params);
echo $response['_source']['MACHINE_ID'];
geetting the same error
root@logging-elastalert:~/elastic_php# php index.php
Fatal error: Uncaught Elasticsearch\Common\Exceptions\BadRequest400Exception in /root/elastic_php/vendor/elasticsearch/elasticsearch/src/Elasticsearch/Connections/Connection.php:681
Stack trace:
#0 /root/elastic_php/vendor/elasticsearch/elasticsearch/src/Elasticsearch/Connections/Connection.php(640): Elasticsearch\Connections\Connection->tryDeserializeError(Array, 'Elasticsearch\\C...')
#1 /root/elastic_php/vendor/elasticsearch/elasticsearch/src/Elasticsearch/Connections/Connection.php(561): Elasticsearch\Connections\Connection->tryDeserialize400Error(Array)
#2 /root/elastic_php/vendor/elasticsearch/elasticsearch/src/Elasticsearch/Connections/Connection.php(262): Elasticsearch\Connections\Connection->process4xxError(Array, Array, Array)
#3 /root/elastic_php/vendor/react/promise/src/FulfilledPromise.php(25): Elasticsearch\Connections\Connection->Elasticsearch\Connections\{closure}(Array)
#4 /root/elastic_php/vendor/guzzlehttp/ringphp/src/Future/CompletedFutureValue.php(55): React\Promise\FulfilledPromise->then(Object(Closu in /root/elastic_php/vendor/elasticsearch/elasticsearch/src/Elasticsearch/Connections/Connection.php on line 681
if I tried this same cert with curl it works fine with -k option
see this
root@logging-elastalert:/var/www/411# curl -XGET -k --cert cert.pem "https://logging-es:9200/.operations.2017.12.06/com.redhat.viaq.common/AWAqLKx4unTnyFKFOn8j"
{"_index":".operations.2017.12.06","_type":"com.redhat.viaq.common","_id":"AWAqLKx4unTnyFKFOn8j","_version":1,"found":true,"_source":{"systemd":{"t":{"MACHINE_ID":"e869c2e3006341c79743d1005f9c8281","BOOT_ID":"9a8eb5fcac8843c2ae10ed2d4da48689","CAP_EFFECTIVE":"1fffffffff","CMDLINE":"/usr/bin/openshift start node --config=/etc/origin/node/node-config.yaml --loglevel=8","COMM":"openshift","EXE":"/usr/bin/openshift","GID":"0","HOSTNAME":"qadatanode2","PID":"9079","SELINUX_CONTEXT":"system_u:system_r:init_t:s0","SYSTEMD_CGROUP":"/system.slice/origin-node.service","SYSTEMD_SLICE":"system.slice","SYSTEMD_UNIT":"origin-node.service","TRANSPORT":"stdout","UID":"0"},"u":{"SYSLOG_FACILITY":"3","SYSLOG_IDENTIFIER":"origin-node"}},"hostname":"qadatanode2","message":"00000160 6e 65 74 65 73 2e 69 6f 2f 6f 73 12 05 6c 69 6e |netes.io/os..lin|","pipeline_metadata":{"collector":{"ipaddr4":"10.131.2.36","ipaddr6":"fe80::2895:c4ff:fe58:c136","inputname":"fluent-plugin-systemd","name":"fluentd openshift","received_at":"2017-12-06T04:49:39.000000+00:00","version":"0.12.37 1.6.0"}},"level":"info","@timestamp":"2017-12-06T04:49:39.000000+00:00"}}
What could be the issue.
Issue was due to authentication error. let me describe it in details if someone else face this issue can be solved it easily.
Requirements were to integrate etsy/411 alert tools with elasticsearch v2.4.4 installed by aggregate logging in Openshift Origin setup to keep records of all the logs of Openshift infrastructure.
Problem: In aggregate logging in openshift, elasticsearch is setup with authentication with secret created in logging project on https URL. We can access elasticsearch with secrets keys,cert and ca cert only. I was able to access elasticsearch on https with these cert keys files with curl command with -k option, due to self sign certificates in openshift.
I was trying to create a bundle cert file by copying key+cert+ca in a single file of the elasticsearch user secret with ssl_cert option as mentioned in docs of etsy/411. But I was able to access it from etsy/411 web app.
Then I search on elasticsearch/php module https://github.com/elastic/elasticsearch-php on github for some help. There some one was asking to use key and cert file to pass authentication in build-connection then some reply to use
->setSSLCert($myCert)
->setSSLKey($mykey)
above two option for cert and key files and ->setSSLVerification($myCa) option is for CA certificate verification. Then I figure out that we are passing ->setSSLVerification($ssl_cert) only in etsy/411 which is for ca cert only and we are missing the client cert and key file for authentication. Thanks for @kiwiz to point me right direction in above comments.
Then I made the below change in two files and it start authenticating to elasticsearch.
Change in /var/www/411/phplib/Search/Elasticsearch.php
if(!is_null($cfg['ssl_ca'])) {
$cb->setSSLVerification($cfg['ssl_ca']);
}
if(!is_null($cfg['ssl_cert'])) {
$cb->setSSLCert($cfg['ssl_cert']);
}
if(!is_null($cfg['ssl_key'])) {
$cb->setSSLKey($cfg['ssl_key']);
}
Changes in /var/www/411/phplib/ESClient.php:
if(!is_null($escfg['ssl_ca'])) {
$cb->setSSLVerification($escfg['ssl_ca']);
}
if(!is_null($escfg['ssl_cert'])) {
$cb->setSSLCert($escfg['ssl_cert']);
}
if(!is_null($escfg['ssl_key'])) {
$cb->setSSLKey($escfg['ssl_key']);
}
As shown above in both the above files I added the option for setSSLCert and setSSLkey option for client cert and key files.
My config.php
# Configuration for the 411 Alerts index.
'alerts' => [
'hosts' => ['https://logging-es:9200'],
'index_hosts' => [],
'ssl_cert' => '/var/www/411/elscert.pem',
'ssl_ca' => '/var/www/411/ca.pem',
'ssl_key' => '/var/www/411/elskey.key',
'index' => null,
'date_based' => false,
'date_interval' => null,
'date_field' => 'alert_date',
'date_type' => null,
'src_url' => null,
],
# Configuration for the logstash index that 411 queries.
'logstash' => [
'hosts' => ['https://logging-es:9200'],
'index_hosts' => [],
'ssl_cert' => '/var/www/411/elscert.pem',
'ssl_ca' => '/var/www/411/ca.pem',
'ssl_key' => '/var/www/411/elskey.key',
// 'index' => '[.operations.]Y.m.d',
'index' => null,
'date_based' => false,
'date_interval' => 'd',
'date_field' => '@timestamp',
'date_type' => null,
'src_url' => null,
],
Now it is working nicely now.
@aaryabhatt Could you submit a PR with these changes?
Hi Kiwiz, I am on leave for some days will submit the PR after 24th of JAN.
Hi @aaryabhatt do you still want to submit a PR?