Displays a summary (warnings, errors, etc...) of your raspibolt's environment.
The script requires sudo or root privileges in order to access the logs.
To run the script you'll need to fill in following variables:
Location where Bitcoin's data files are stored:
pathBitcoin="PATH/TO/BITCOIN/DATA/FOLDER"Integer. Default: 48 (hours). The value will be saved in the variable hoursAgo.
Look for events in the last day:
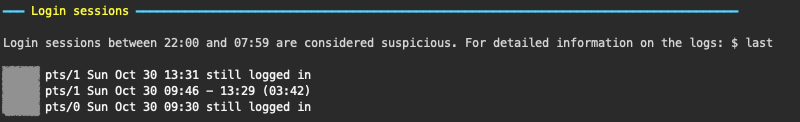
$ sudo bash report.sh 24Displays closed and active login sessions.
Logins between 22:00 and 07:59 will be considered suspicious and therefore marked in red. If you want to use different hours, you'll have to modify the RegExp.
Active sessions will we marked in red as well.
Command used to access the logs (see hoursAgo in Arguments):
$ last -R -s "-${hoursAgo}hours"
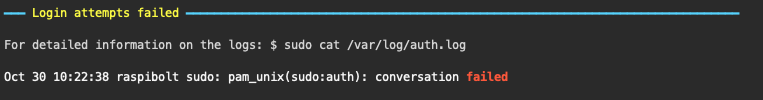
Log entries that match the RegExp Failed|Failure|preauth|Connection closed will be displayed.
Command used to access the logs:
$ cat /var/log/auth.log
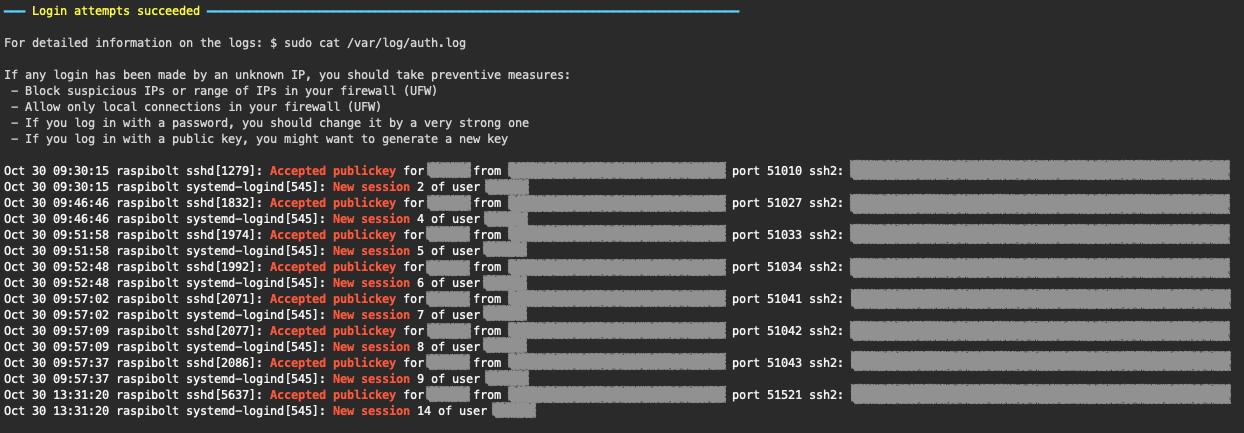
Log entries that match the RegExp New session|Accepted password|Accepted publickey will be displayed.
If a successful connection using a password is detected, a warning message will be displayed so that the user considers logging in using a public key.
Command used to access the logs:
$ cat /var/log/auth.log
Log entries that match the RegExp fail2ban\.actions will be displayed.
If the file /etc/fail2ban/fail2ban.conf is not found in your system, a warning message will be displayed.
Command used to access the logs:
$ cat /var/log/fail2ban.log
Additionally, statistics about failed and banned actions will be displayed:
$ sudo fail2ban-client status sshd
Displays firewall connection attempts excluding broadcast connections "224.0.0." and lines containing 'UFW AUDIT'.
If the file /etc/ufw/ufw.conf is not found in your system, a warning message will be displayed.
Command used to access the logs:
$ cat /var/log/ufw.log
Log entries that match the RegExp error|warn(ing)? will be displayed.
Command used to access the logs (see pathBitcoin in Bitcoin's path):
$ cat "${pathBitcoin}debug.log
Log entries that match the RegExp error|warn(ing)? will be displayed.
Command used to access the logs (see hoursAgo in Arguments):
$ journalctl -u electrs --since="${hoursAgo} hours ago"
Tor Hidden Services
Entries that match the RegExp ^HiddenServiceDir will be displayed.
Command used to access tor configuration:
$ cat /etc/tor/torrc
Services that failed to start.
Command used:
$ systemctl list-units --failed