CDK Pipelines security posture change approvals
eladb opened this issue · comments
| PR | Champion |
|---|---|
| # |
Description
The default behavior of CDK Pipelines should ensure that a change in the application's security posture is explicitly approved.
CDK applications normally include security-related infrastructure definitions such as networking rules an IAM policies. Changes to these definitions may expose the application to security risks. Such changes can happen as a result of a change in the application code or they can happen as a result of changes in a 3rd party construct library the application depends on (or a transitive dependency thereof).
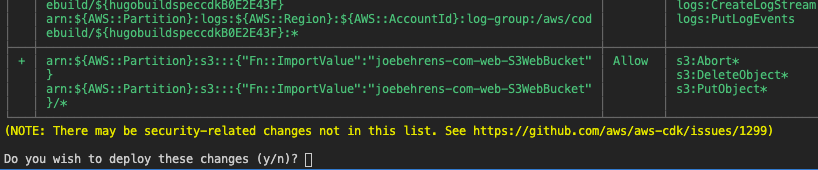
The CDK CLI heuristically detects such changes when cdk deploy is executed based on the "diff" between the currently deployed application and the application that's about to be deployed. A report is printed and an explicit confirmation is required:
The current implementation of CDK Pipelines bypasses this confirmation dialog using a CLI switch (--require-approval=never). This means that a commit to the source repository that changes the security posture of the application will be deployed automatically to the target environments.
CDK Pipelines allows users to add approval steps to their flow. This means that users are technically able to block their deployments and review any changes, but the default behavior must be safe and secure.
Progress
- Tracking Issue Created
- RFC PR Created
- Core Team Member Assigned
- Initial Approval / Final Comment Period
- Ready For Implementation
- implementation issue 1
- Resolved
Ideas for solutions
- At the minimum, we can change the default so that pipelines are always blocked from deploying to production (we need to identify "prod" stages in order to do that). This will require that users will always review the diffs before deploying to production.
- Require that a user with read-only access to all production environments will commit a file to the repo that approves changes. The benefit of such an approach is that it is deployment-system-agnostic.
@otaviomacedo @rix0rrr What's the status of this one?
It was addressed by this commit.