An opinionated Azure Kubernetes Service (AKS) cluster for running demo apps, leveraging Makefile instead of lots of bash-fu to install AKS add-ons.
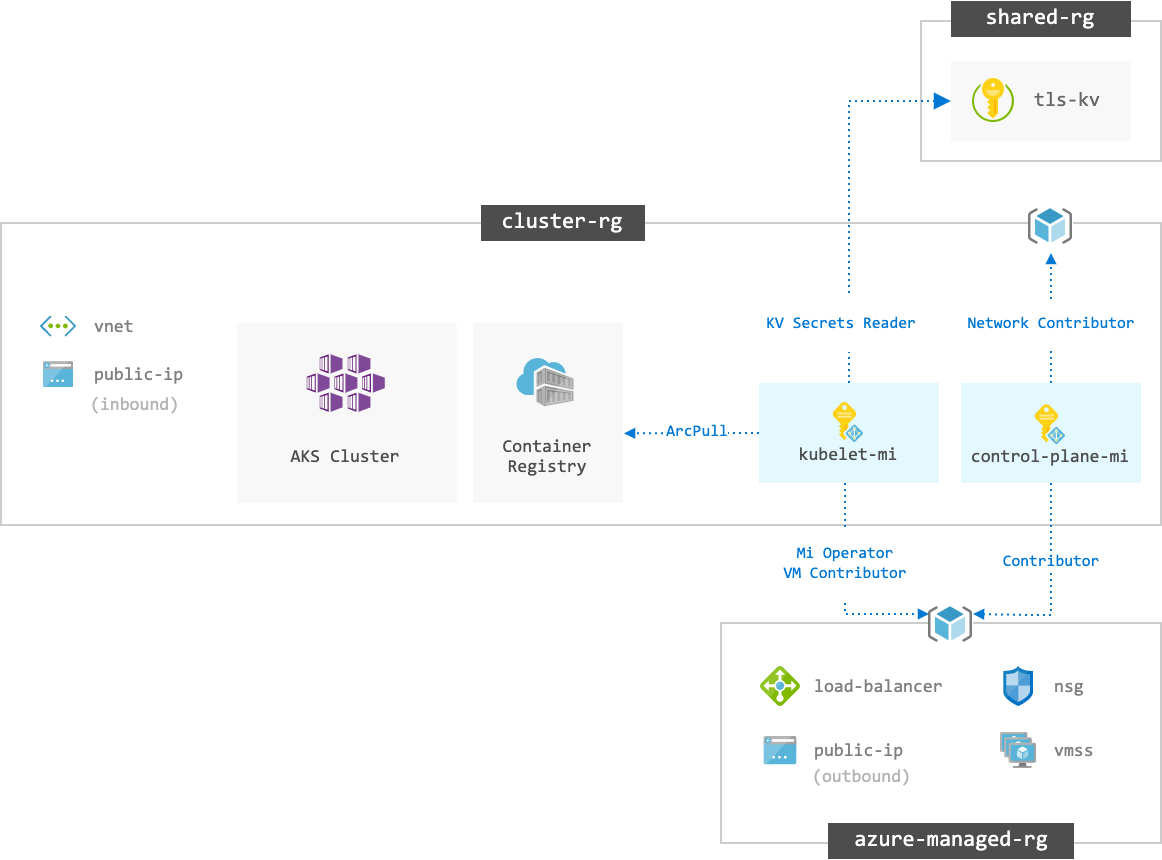
The following diagram illustrates the Azure solution architecture for each cluster, e.g. dev, staging and prod.
- Virtual Network integration
- Azure CNI Networking
- NGINX Ingress Controller
- Prefer
-managed-rgsuffix over defaultMC_prefix for resource group containing managed cluster
| Managed Identity | Security Principal | Details |
|---|---|---|
control-plane-mi |
AKS Control Plane | Interfaces with ARM to manage cluster resources, VMs, networking, etc. |
kubelet-mi |
K8s Node Agent | Needs some access e.g. Container Registry and Key Vault to setup workloads. |
Resources names will include one of
devstagingprod
Using Terraform and make commands, you will have an AKS cluster with all the Azure CSI and Pod Identity Add-Ons up and running with just 5 commands.
In order to deploy AKS clusters using IaC in this repository, you will need the following command line tools:
- terraform
- kubectl
- helm 3
- make
- envsubst
Install on a macInstall on Ubuntubrew install gettext brew link --force gettext
apt-get install gettext-base
The following Azure resources are located in a separate Resource Group cloudkube-shared-rg and managed by the cloudkube-shared-infra repository:
- DNS Records
- Key Vaults
- Role Assignments to access TLS Certificates
Without these resources, the setup of the Ingress controller will fail as it wants to configure TLS encryption.
This is not necessary if you just want to deploy and manage a single cluster from your local machine. In cloudkube.io use case, this infrastructure as code (IaC) repo is used to manage 3 distinct AKS clusters and will be integrated with CI/CD.
And to comply with governance best practices, we have 2 different storage accounts to create a security boundary between production and non-production resources.
Diagram: use different Storage Accounts for RBAC on Terraform State. See backends/README.md for details.
First initialize the remote backend and specify which environment, e.g. backends/dev.backend.hcl
terraform init -backend-config=backends/dev.backend.hclIf you dont' want to deal with remote and multiple environments, you can leave out the -backend-config flag.
Now create a infrastructure plan. Specify environment configuration with var-file flag pointing to e.g. environments/dev.tfvars
terraform plan -var-file=environments/dev.tfvars -out plan.tfplanIf you are satisified with the plan, deploy it
terraform apply plan.tfplanIf the cluster is a re-created, go to julie-ng/cloudkube-shared-infra and run the infra as code there to
- update DNS records to new Static IP
- update RBAC Assignments to Key Vault that holds TLS certificates. Otherwise ingress controller deployment will fail.
When that runs, come back here.
Finally finish cluster setup with
make kubecontext
make setupwhich will
- install Azure CSI driver
- setup namespaces
- install nginx ingress controller
- setup and configure "hello world" app
- configure TLS by pull certificates from shared Key Vault
See Makefile for details.
If an upgrade (e.g. enable Azure RBAC) requires Terraform to destroy and re-create the cluster, then additional steps are required after terraform apply
- re-setup with
make setupwas required - re-setup access to TLS certificates for ingress
- the managed identities for kubelet and ingress change, which requires re-deploying cloudkube-shared-infra.
- then finish setup by re-running failed step
make apply-hello
To update CHANGELOG.md with standard-version run
standard-version --packageFiles manifest.json --sign --release-as minorthen adjust as needed by hand and commit.
Official Documentation
- Terraform Docs - Organizing Multiple Environments for a Configuration
- Terraform Docs - When to use Multiple Workspaces
- Terraform Docs - Variable Definition Precedence
- Azure AD RBAC
- Azure Kubernetes Service - Summary of Managed Identities
- Azure AD Workload Identity with AKS
- Azure CSI
- Kubernetes Docs - NGINX Ingress Controller
- Helm Chart on Artifact Hub
- Helm Chart Source on GitHub.com