This repository contains demonstrations of various security concepts, emphasizing Address Space Layout Randomization (ASLR), stack overflow, and virtual pointer (vptr) vulnerabilities.
- 1️⃣ ASLR Demonstration
- 2️⃣ Stack Overflow Demonstration
- 3️⃣ Integer Overflow Demonstration
- 🗑 Cleaning Up
- 🤝 Contributing
- 🙏 Acknowledgment
⚠️ Disclaimer- 📜 License
- 🧮 CIA: Confidentiality, Integrity, and Availability
ASLR is a computer security technique that randomizes the memory addresses used by processes. This makes it harder for an attacker to predict the location of specific functions or buffers they might target.
-
Toggle ASLR: The program
aslr_exampallows you to turn ASLR on or off on a Linux system. This is useful for visualizing the effects of ASLR on memory address allocations. -
Memory Address Visualization: The program
print_memis a helper utility that prints the memory address of a dynamically allocated variable, demonstrating the effect of enabling or disabling ASLR.
To compile the ASLR demonstration:
make aslr_examp print_memRun the ASLR demo:
./aslr_exampThe program stack_demo highlights vulnerabilities tied to stack overflow and vptr overwrites. By tampering with a class's virtual pointer (vptr), it can redirect its virtual function calls, thereby enabling unauthorized access.
By default, the program uses a predefined buffer to demonstrate the overflow. But you also have the option to feed data manually or pipe it into the program, even though the default method is easier for demonstration purposes.
To compile all the demonstrations at once, simply use:
makeAlternatively, you can use the Gtk GUI to compile the programs individually. To do so, run the following command:
g++ gui.cpp -o gui `pkg-config --cflags --libs gtk+-3.0` -lssl -lcrypto -w -fno-stack-protector -g -no-pie -g3 -DNO_PIEThe program int_overflow demonstrates the effects of integer overflow. It is compiled using the following command:
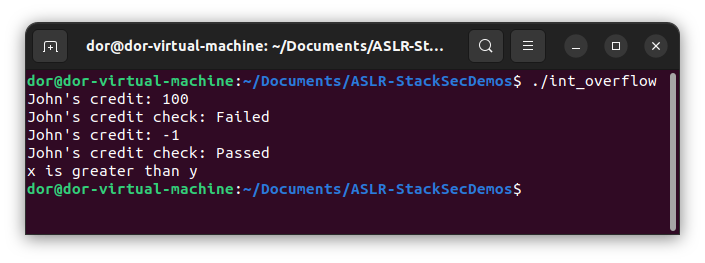
g++ int_overflow.cpp -o int_overflowIn C++ , when comparing an int to unsigned int, the int is converted to an unsigned int. This means that if the int is negative, it will be converted to a large positive number. This can lead to unexpected results, as demonstrated in the program.
int main() {
int x = -1;
unsigned int y = 1;
if (x < y) {
std::cout << "x is less than y" << std::endl;
} else {
std::cout << "x is greater than y" << std::endl;
}
return 0;
}To clean up and remove the compiled binaries:
make cleanIf you'd like to contribute to this project, please fork the repository and submit a pull request.
The code examples in this repository are inspired by and built upon concepts studied in the Open University course "Defensive System-Programming (20937)".
The code in this repository is strictly for educational purposes. The demonstrated vulnerabilities aim to raise awareness and understanding of potential security risks. Do not use the code maliciously or without proper understanding. Ensure that you have necessary permissions before making system-level changes, such as modifying ASLR settings.
This project is open-source and is licensed under the MIT License, which is available in the LICENSE file.
From "Modern Operating Systems" by Andrew S. Tanenbaum
-
Confidentiality: Ensuring information is not disclosed to unauthorized individuals, entities, or processes.
-
Integrity: Maintaining the accuracy and completeness of information.
-
Availability: Ensuring information is accessible and usable upon demand by an authorized entity.
| Criteria / Service | Confidentiality | Integrity | Availability | Example Use Cases |
|---|---|---|---|---|
| Popular News Services | ✘ | ✔ | ✔ | Access to news, not typically confidential |
| Backup Storage Systems | ✔ | ✔ | Moderate | Secure storage, not always instantly available |
| Banking Services | ✔ | ✔ | ✔ | High standards for sensitive financial data |